Linux graphical encryption program
VeraCrypt is probably the most user-friendly and the most flexible Linux graphical encryption program. So, in this post, I will show you how to use it.
INTRODUCTION
I previously showed you how to encrypt the hard drive in Linux with a command line tool, in this post, I will show you how to make encryption in Linux with a beautiful graphical program. This program is called VeraCrypt.
VeraCrypt - the best Linux graphical encryption program
If you used the encryption on Linux before, you probably have heard about the program TrueCrypt. If you have not, TrueCrypt was a graphical utility for encrypting folders and partitions to protect your data. However, it is not secure anymore and it is not developed anymore. VeraCrypt is a current alternative of TrueCrypt.
VeraCrypt is an open source software application, which serves to encrypt and hide data that a user considers confidential. It uses fairly current and secure encryption protocols. And for me, it is the best Linux graphical encryption program.
VIDEO TUTORIAL
How to install VeraCrypt
First, download the Linux version from the official VeraCrypt website. By the way, VeraCrypt is cross-platform, so, you can install it on Windows, Linux, Mac OS, and FreeBSD.
Then, open your file browser, select the downloaded file and right click on it and extract the archive.
Open a terminal and change the current directory to the folder generated by the decompression and list all the files.
cd Downloads/veracrypt-*-setup/ ls -l
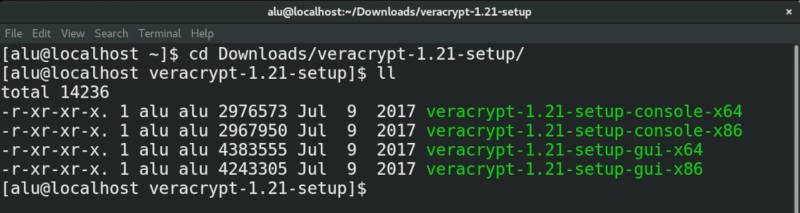
Among all the files, you should see a file gui
So, to start the installation, you run this command:
sudo ./veracrypt-X.XX-setup-gui-x64
Then, you have to choose the installation option. Type 1 to install Veracrypt.
Next, it is necessary to accept the license terms. Type yes to accept.
After accepting the license terms, the program will start the installation. In the end, you should see a message on the terminal saying Press Enter to exit.
To run it, just type veracrypt from your terminal and press enter. Of course, you can also launch it from the main menu of your system.
This is what the program looks like once you have started it. It is a very simple interface but it is very powerful.
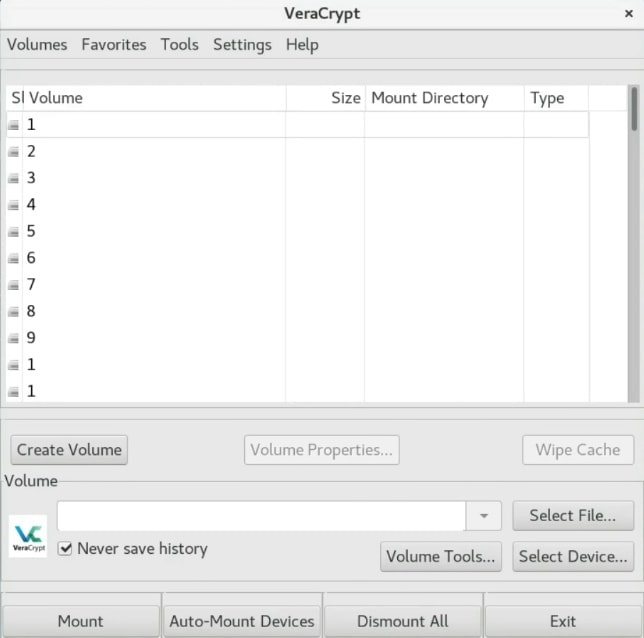
Create an encrypted VeraCrypt volume
Now it is time to create a VeraCrypt volume. Click on the Create Volume button.
You can just create an encrypted file container. In short, it is a virtual folder which is encrypted. Or you can also encrypt the whole partition or the whole drive. Choose whatever you want the principle is basically similar for the two options. In this example, I will just create an encrypted container.
Create an encrypted container
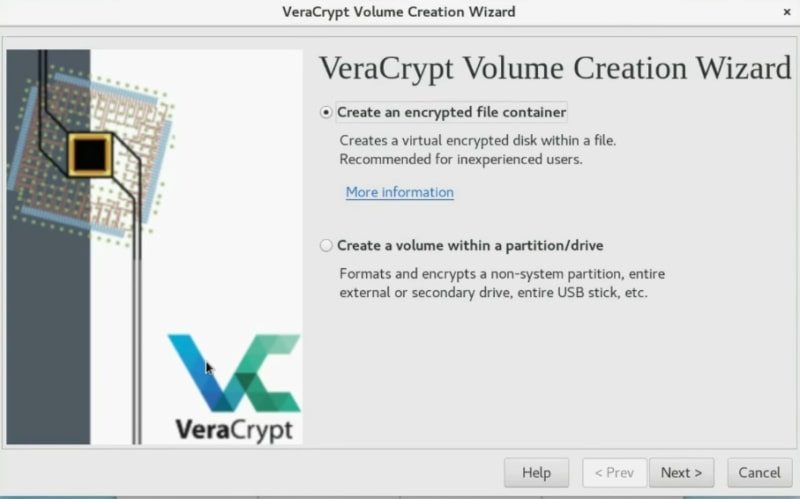
In the next screen, I suggest you use a standard VeraCrypt volume but if you want more security, you can use the hidden volume option. I will choose to create a Standard VeraCrypt volume.
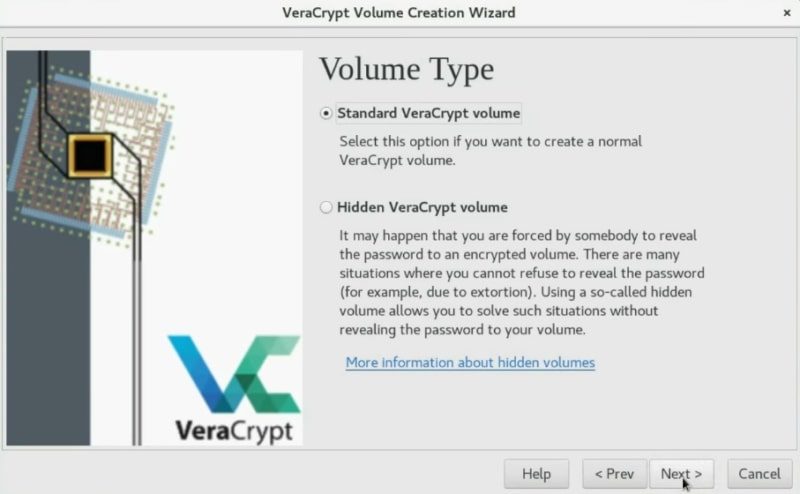
In this section, you have to select where you want this encrypted volume to be located. Click on the Select File button and set the place and name. After that, click on the Next button.
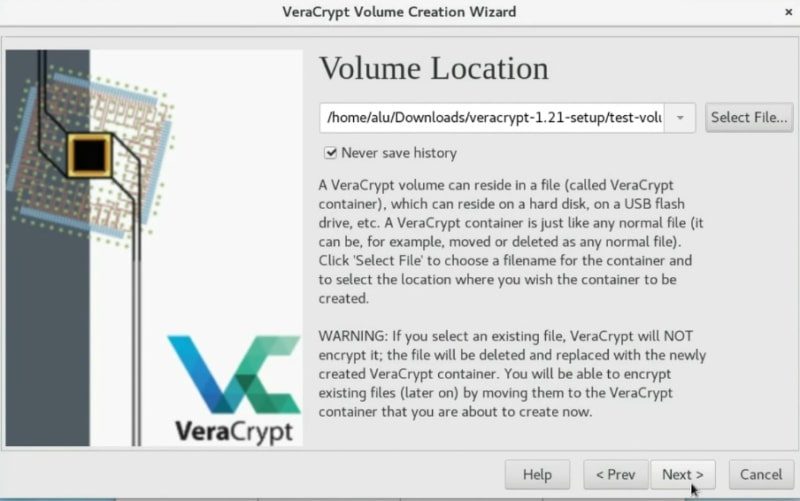
VeraCrypt provides several encryption algorithms like AES, Twofish or Camellia. I usually choose AES. This should be secure enough. Click on the Next button.
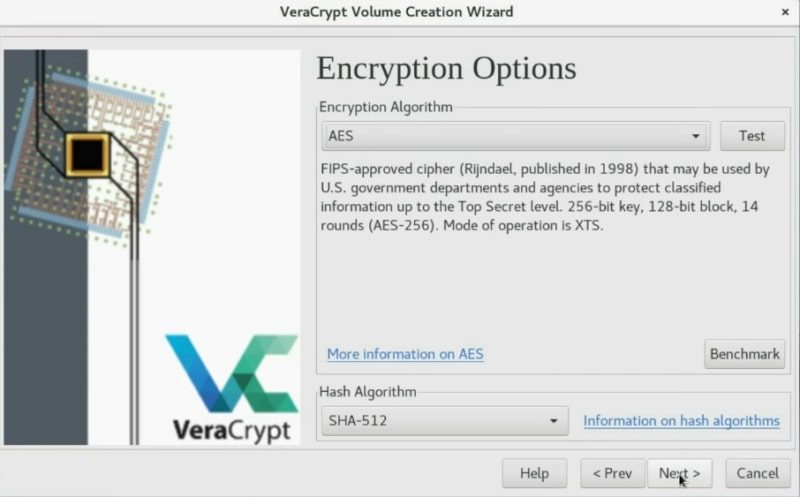
Now, you have to define the space of the container. Veracrypt shows you how much disk space is available and you can create a volume of this size or smaller. In my case, I will create a 1Gb volume.
Choose a security level (password, PIM, keyfile)
Now, it is time to define your password. It will be used to decrypt the volume. You have to define a very strong one.
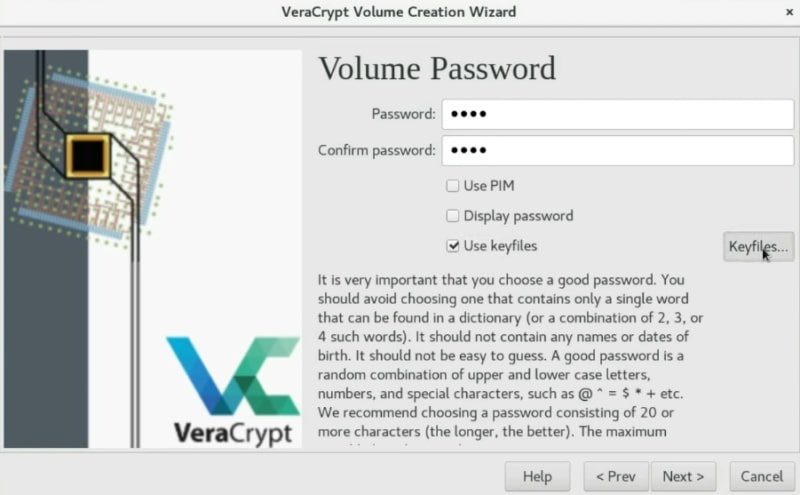
Usually, setting a password is secure enough. However, if you want to be your encryption as secure as possible, you can also enable the PIM option, this means you just need to specify a specific number during the mounting process. I never use it. If you want more security I recommend you to use a key file. This is a very useful option. So, I will create a KeyFile to show you the process.
Create a KeyFile
To create a key file, just click on the Generate random key file button.
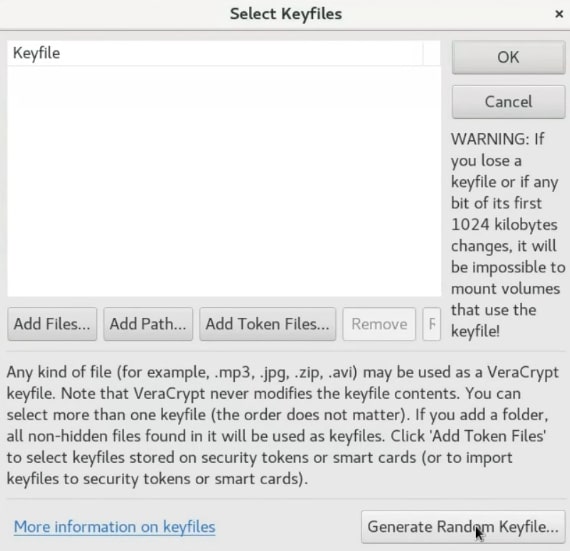
You need to move your mouse randomly as much as possible to create some random numbers which will be stored in this key file. You can move it until the Randomness bar is completely full. After that, you give it a name, click on the Generate and Save Keyfile option and choose a place to save it.
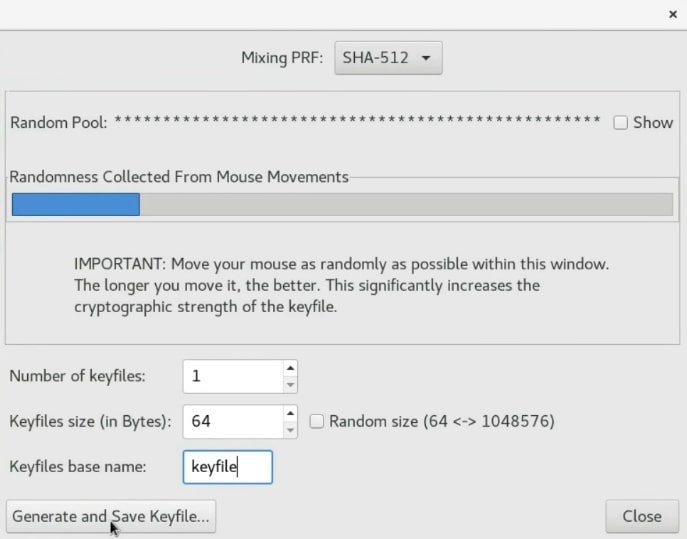
Once the /home/alu/Download/. So, Click on the add button and select the keyfile.
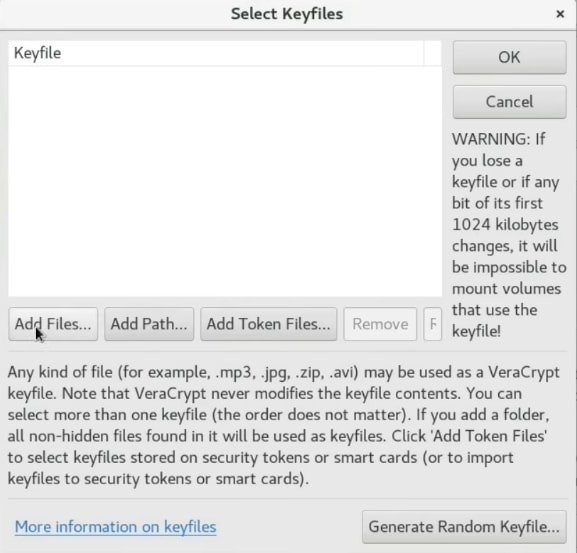
Next, press the OK button.
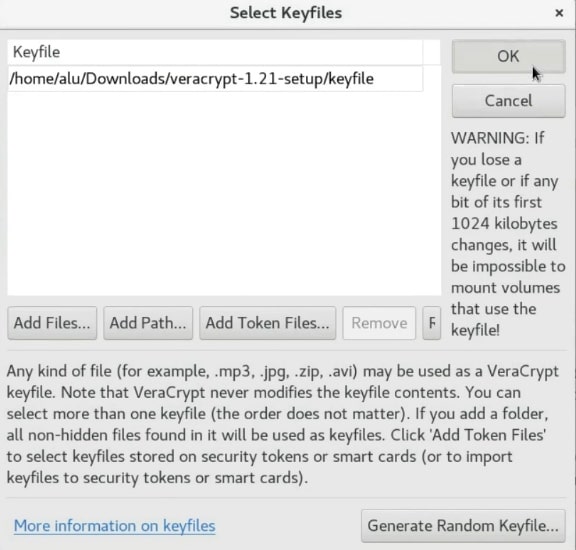
Now, to unencrypt this volume you have to use the password and in addition to this, you also need to use a key file. I recommend storing the
NOTE that If you lose your key file you will not be able to unencrypt this volume. So, make sure you have a backup of this key file.
Next, click on the Next button.
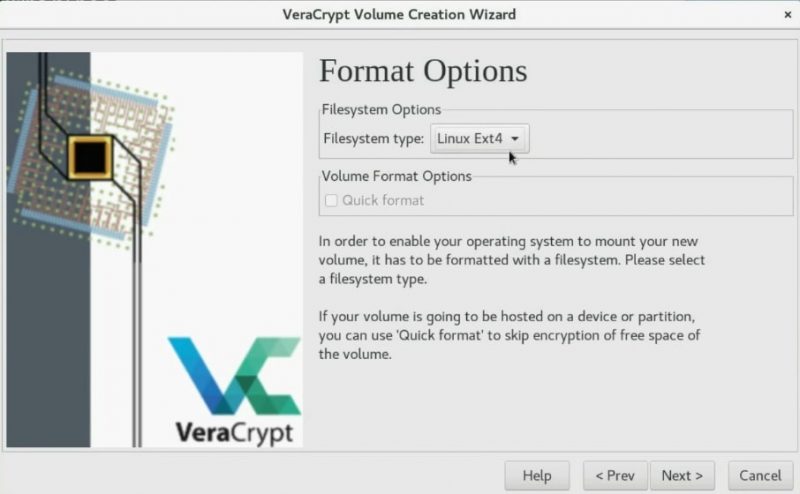
Choosing a new filesystem for the volume
Using a Linux graphical encryption program, you can set the file system for the new volume system. So, If you are going to mount the volume in Windows and Linux, you should choose FAT, but if you will only use it for Linux you can choose EXT4.
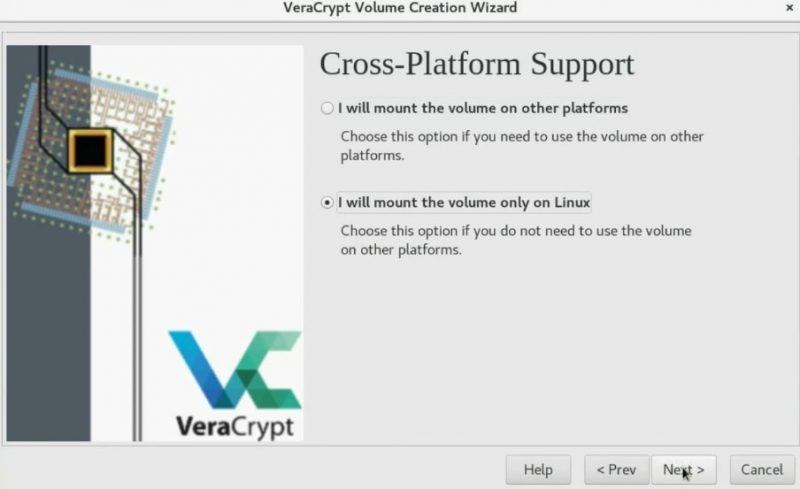
In the next screen, you can choose if you want to mount this encrypted volume on different systems or only on Linux. The former option enables cross-platform compatibility of the encrypted volume.
Encrypting the volume
To encrypt the volume, you need to generate some randomness by moving your mouse as random as possible in the next screen. So, wait until the bar is completely filled. Next, click on the Format button.
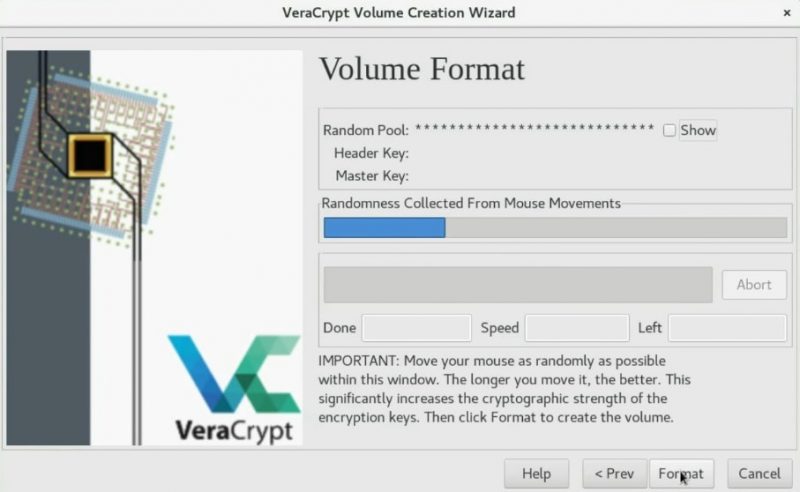
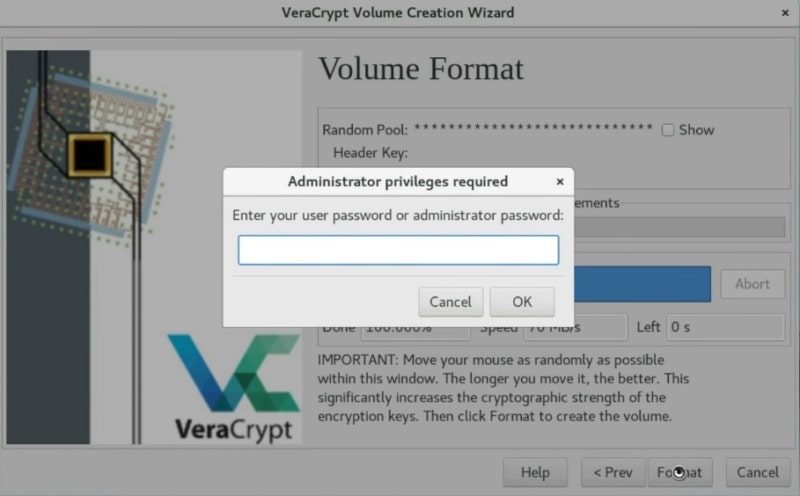
You may also need to type your root password during this process.
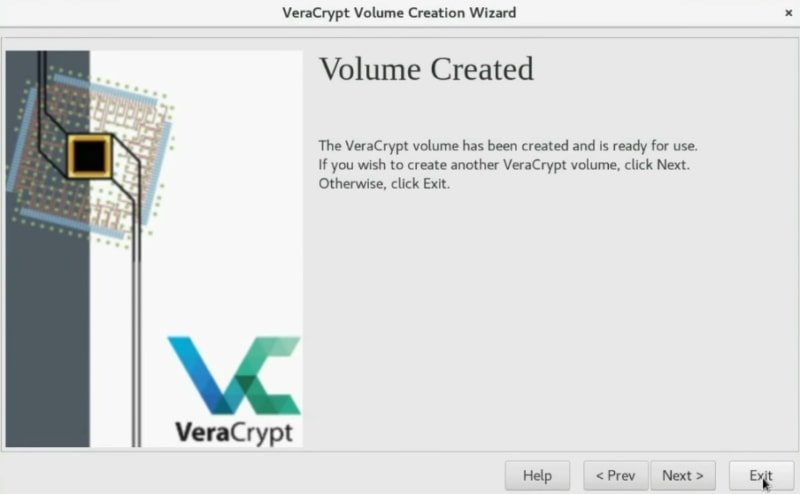
In the end, you should see the screen saying that the volume has been successfully created. So, you can start using this Linux graphical encryption program.
Mounting the newly created volume to test it
After you created the encrypted volume, you need to mount it. First, we need to select the volume. So, click on the Select File option.
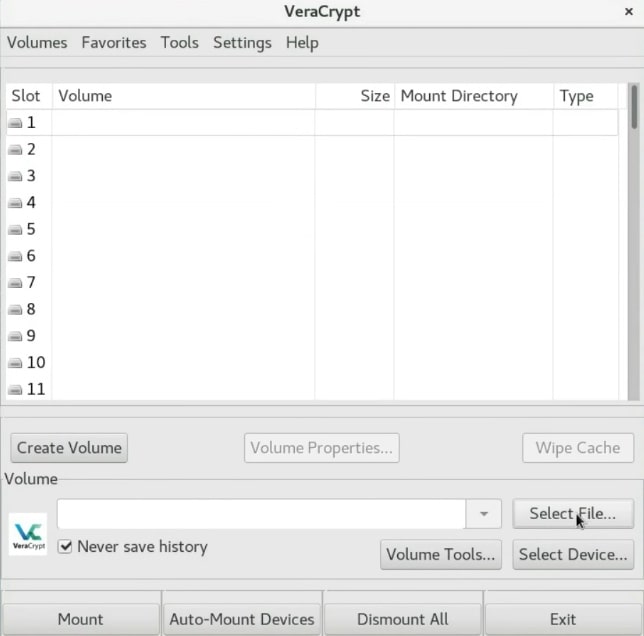
Next, navigate and select your volume.
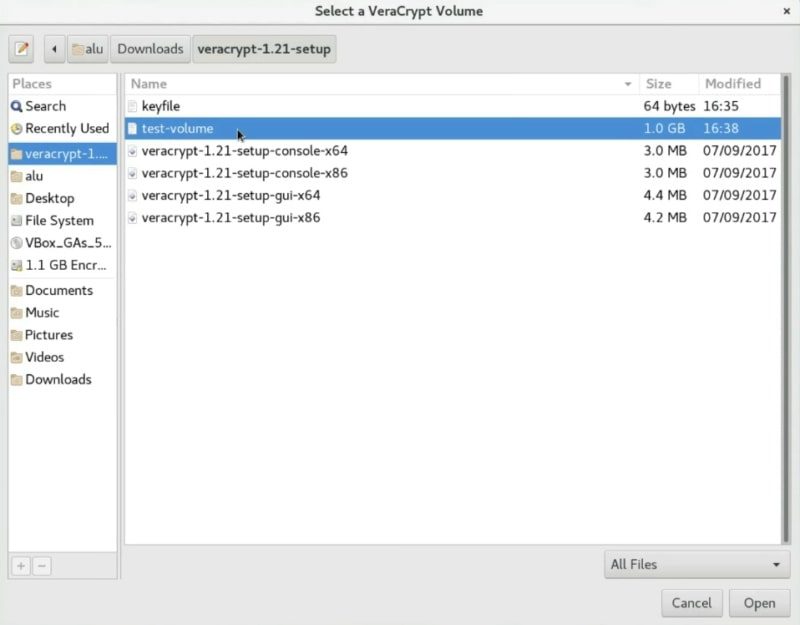
After that, you need to select where you want to mount it. Just select the first slot and click on the Mount button.
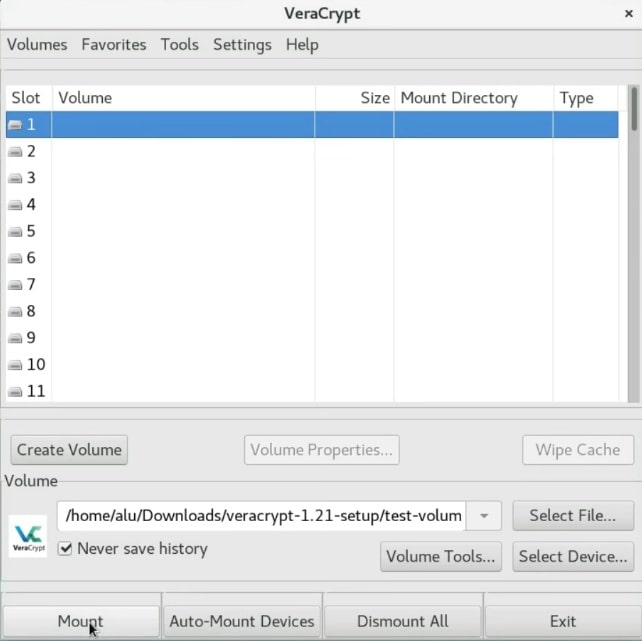
In this screen, you have to enter the password you used for your encryption. If you encrypted this container with a
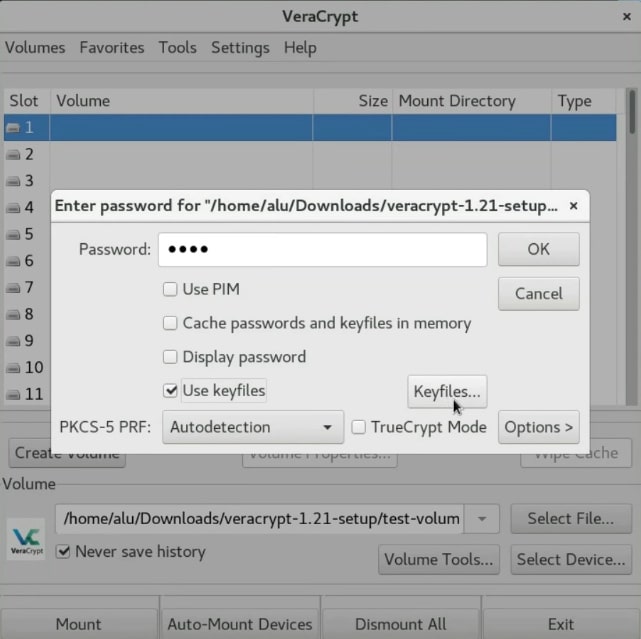
After that, the volume should mount to the /media folder.
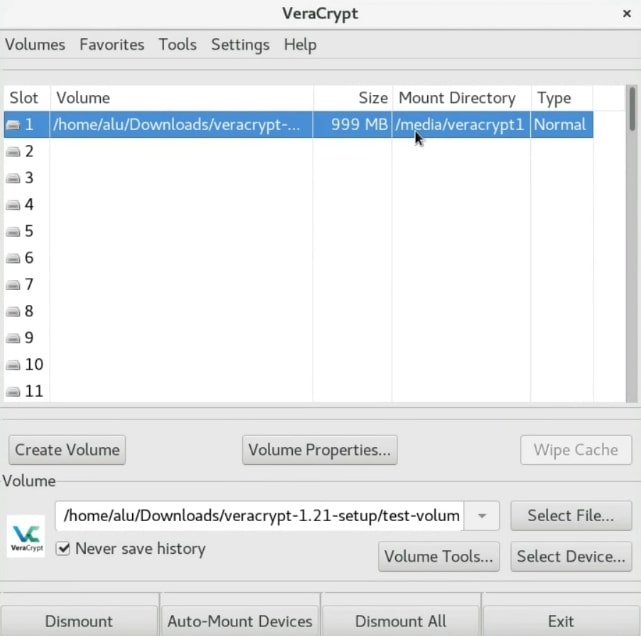
You can see that it is mounted /media/veracrypt1/media/veracrypt1
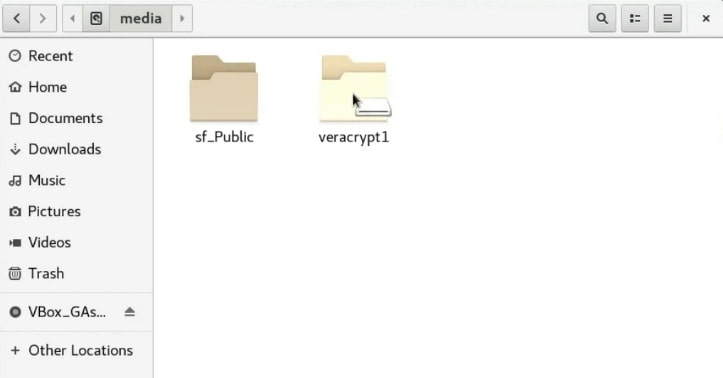
And there is the encrypted volume. You can copy all the files you want to encrypt to this veracrypt1 folder.
Unmounting the encrypted volume
After you finished placing the information to the encrypted volume, you have to close the file manager and unmount it.
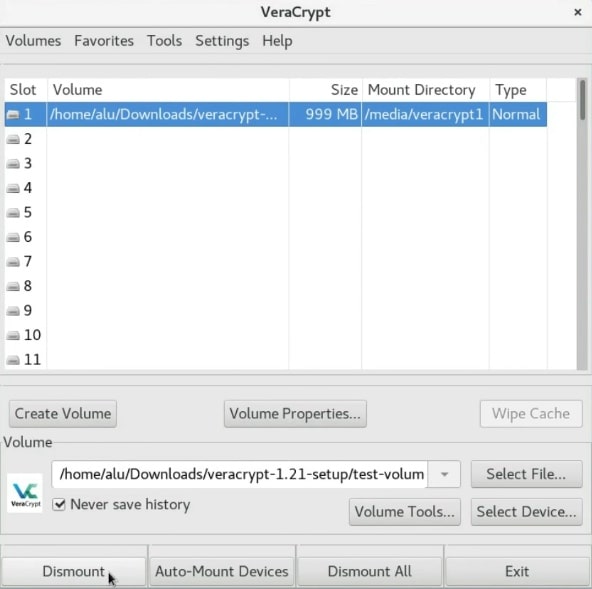
So, on the VeraCrypt window, select the volume and click on the Dismount button.
Then, you can close the program by clicking on the Exit button.
Uninstall VeraCrypt
If you no longer want to use VeraCrypt and need to uninstall it, first enter to the Veracrypt folder and run the following command in the terminal.
sudo veracrypt-uninstall.sh
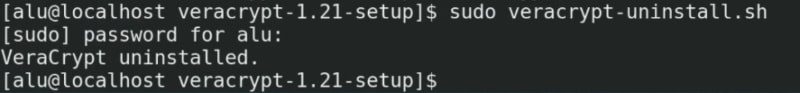
You will need to enter your password and VeraCrypt will be removed from your system.
CONCLUSION
VeraCrypt is a great program not only because it has a graphical interface but also because it is a very powerful encryption tool. I highly recommend you to use it. You can create an encrypted file container, encrypt a whole hard drive or if you want to make your data very secure, you can also create a hidden encrypted partition.
So, do you know another Linux graphical encryption program? Let me now on the comments section.
 Never miss a post from us, subscribe to our newsletter
Never miss a post from us, subscribe to our newsletter
Comments
Kape
Hi Alu, great article, thank you ! Nowadays a lot of talk about so called ransom malware. Are there any possibilities to use VeraCrypt protect my data against possible ransom malware attack ?
Average Linux User
Hi Kape, I am not an expert in this question. Encryption is to hide the data from human. Ransomware blocks access to your files regardless if they are encrypted or not. I would better focus on what links you click and what programs you install to avoid ransomware
Kape
Alu, thank you very much for your reply and important clarification !
Sam Moss
Haven't found the answer but I do find your posts here and on YouTube very useful. Thanks again.
Average Linux User
Sorry for not being able to help :-( Thanks for visiting this website and youtube channel.
Sam Moss
thanks…that question came up when I created a container (using your tutorial btw) on a friends PC. it would seem logical that after a container was decrypted that a program should be able to run in that container. as a matter of fact the app in question is Portable Apps. being new to Linux Mint the more I work with it the better I like it….thanks for your time an input 👍
Average Linux User
I am glad you found the answer. BTW, you may find useful my posts on Linux Mint.
Sam Moss
Thanks it (Snaps) was in the Software Package listed as snapd. As far as you know tho can a program or app be run inside the container itself? Ever heard of doing that? Is it possible?
Average Linux User
Maybe I do not get your question. If you ask about a VeraCrypt container, I think a portable version of a program will run from an encrypted volume when it is decrypted and mounted.
Sam Moss
Saw your video first on 'how-to' then saw this site; both really came in handy. Good job. 👍 Question: Is there a way to run programs or applications inside the Linux Mint container? Can a package in the Software Manager be downloaded in the container?
Average Linux User
You probably need Snaps
David Yentzen
Hi, great article and video on Veracrypt. I personally use zuluCrypt and I am hoping you'll consider doing a separate tutorial on using it. https://mhogomchungu.github.io/zuluCrypt/ Thanks and I do find your videos and articles helpful!
Average Linux User
I will try to check it. Thanks.
michael biller
Great article. VeraCrypt is fantastic and so is this guide on using it. Thanks
Average Linux User
Thank you, Michael!
Silvio
Hi Alu, this article of yours is interesting as usual, thank you. Encryption is important to be sure that some files or folders can be open only by the owner and I have been looking around for a solution; VeraCrypt comes out as number one solution but the project is abandoned if I remember properly. So, looking for other solution I found “gpg”. Please, can you tell me if files or folders are safe using it? I mean: $ gpg -c test.txt # creates the encrypted file (asking pw twice) $ gpg test.txt.gpg # open the encrypted file Same for folders but needing to compress them (.zip .tar.gz etc.) before starting the gpg process. Is gpg enough to be sure that no one can access personal files? Ciao :)
Average Linux User
1. What makes you think VeraCrypt is abandoned? It is actively developed, check their website. Probably, you mix VeraCrypt with TrueCrypt. The latter was abandoned. 2. I have not tried gpg, so I cannot comment on it.