Encrypt your Hard Drive in Linux
Do you need to encrypt a hard drive in Linux? This post will show you how to encrypt a separate partition, a whole hard drive, or just a USB stick. It will work in any Linux distribution.
There are many methods to perform encryption in Linux. In this post, I will show you the encryption method I use the most. It is probably the simplest method to encrypt your data in Linux. It is a command line tool, but there is nothing extraordinary.
Encrypt your hard drive in Linux with LUKS
I usually use LUKS encryption and dm-crypt.
Install the necessary programs
First, you need to install cryptsetup package:
sudo apt install cryptsetup
Identify the partition name
Next, make sure the partition you are going to encrypt doesn’t have any important data on it because it will be overwritten during the encryption process.
If your hard drive is brand new, you may need to create a new partition table. If you want to encrypt only part of your hard drive, you also need to re-partition your hard drive into two partitions: one will be encrypted and another one won’t. You can use Gparted for that.
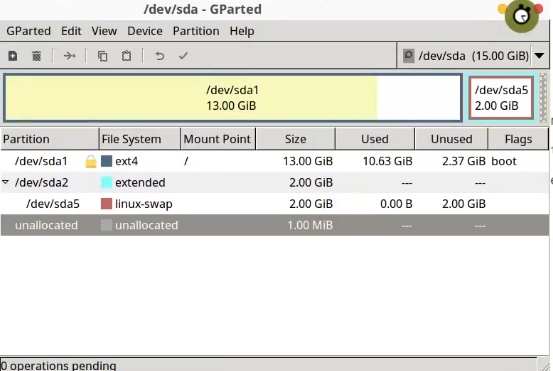
You can also find out the name of your partition with the command lsblk and find the partition you need based on its size.
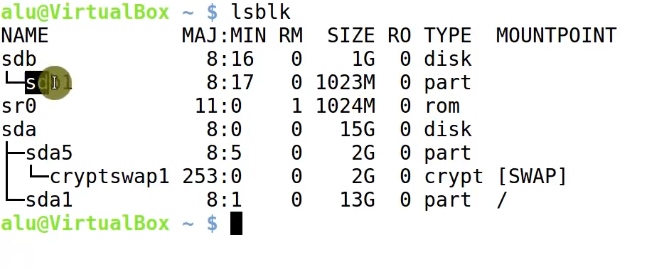
Encrypt this partition
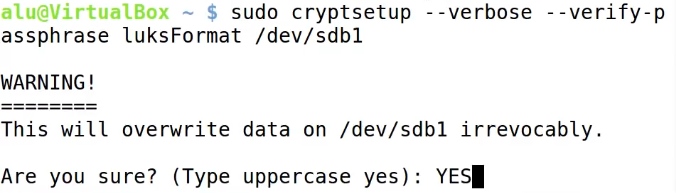
When the partition you want to encrypt is ready and all the data is backed up into another hard drive, run this command:
sudo cryptsetup --verbose --verify-passphrase luksFormat /dev/sdb1
Where /dev/sdb1 is the partition you want to encrypt. Next, confirm that you agree to overwrite all the data in this partition.
Next, you will be prompted to type your passphrase. When you type it, you will see nothing. This is normal and due to security reasons. You will need this password to unencrypt the partition. Make sure you memorize it.
Next, open the encrypted partition. This is where you will need to type your passphrase.
sudo cryptsetup luksOpen /dev/sdb1 sdb1
Once the partition is opened, the encrypted partition is mapped to /dev/mapper/sdb1.
sudo fdisk -l
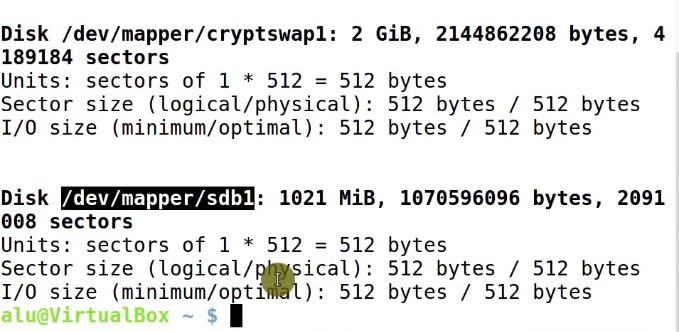
Then, create a new filesystem on it:
sudo mkfs.ext4 /dev/mapper/sdb1
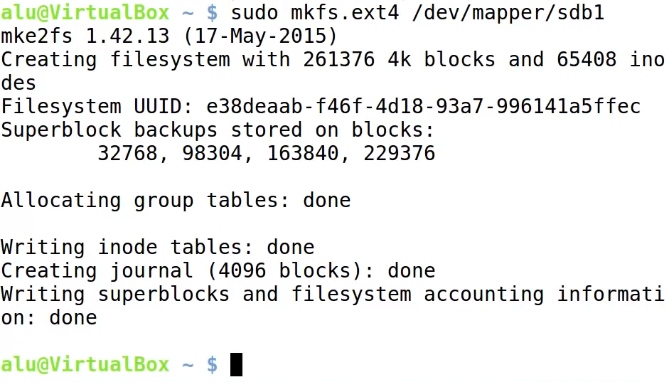
I also suggest to get rid of reserved space. EXT4 file system reserves some space by default, but you won’t need it if you don’t run your system on this partition. This way you also get more space on the drive:
sudo tune2fs -m 0 /dev/mapper/sdb1
Now, your partition is encrypted and ready to use.
Test the encrypted partition
Mount it somewhere on your system. /mnt is the most common place to mount partitions.
Let’s create a folder encrypted in it.
sudo mkdir /mnt/encrypted
And perform the mounting:
sudo mount /dev/mapper/sdb1 /mnt/encrypted
Now, you can start placing your files into it. However, you will be able to do that only with sudo because regular users do not have access to this folder.
Let’s change the ownership of this encrypted folder, to give access to regular users:
sudo chown -R `whoami`:users /mnt/encrypted
Now test it by create a file as a regular user without sudo.
touch /mnt/encrypted/test.txt
You can also create and view encrypted files, from your file manager:
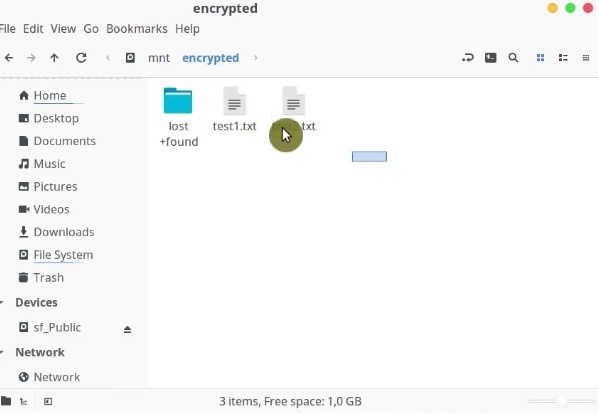
When you finish working with the encrypted partition, unmount it.
sudo umount /dev/mapper/sdb1
Let me remind you that my encrypted partition name is sdb1, in your case it may be different.
Then, close the mapped device.
sudo cryptsetup luksClose sdb1
Finally, it is safe to disconnect the hard drive from your system.
How to use the encrypted hard
Next time, when you want to use your encrypted drive. You have to connect your hard drive to the system and check its name.
lsblk
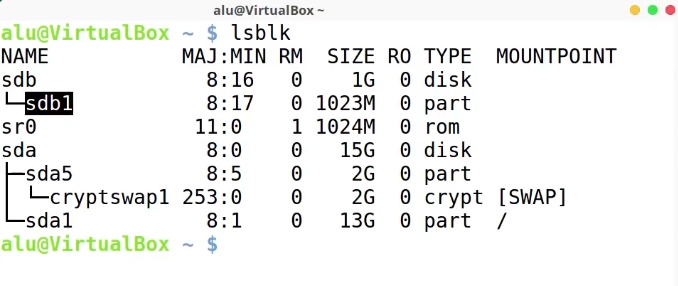
It is sdb1 in my case.
Next, open the encrypted partition with your decryption password:
sudo cryptsetup luksOpen /dev/sdb1 sdb1
Then, mount it.
sudo mount /dev/mapper/sdb1 /mnt
Now, it is available at /mnt/encrypted. As you can see, the test files we created earlier are there.
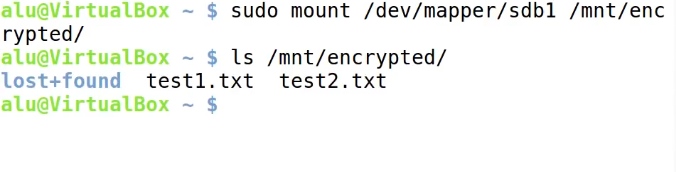
When you finished working with this encrypted files, unmount the partition:
sudo umount /dev/mapper/sdb1
And close it.
sudo cryptsetup luksClose sdb1
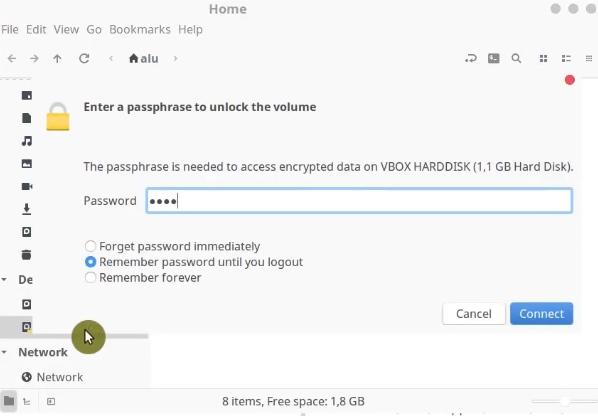
In some Linux systems, such Linux Mint in my case, you can also mount the encrypted partition by double-clicking on it in the file manager and entering your passphrase. So, you can avoid the command line hassle.
Conclusion
This way you can encrypt any hard drive, including flash drives. If you encrypt a hard drive that is permanently connected to your system, you can also make it mount automatically on the boot of your system.
For the next read, I recommend you my post about Linux Root Folders.
So, do you use an encrypted partition? What method do you use to encrypt it? Let me know below.
 Never miss a post from us, subscribe to our newsletter
Never miss a post from us, subscribe to our newsletter
Comments
Nigel Horne
The mount command fails with:
unknown filesystem type ‘crypto_LUKS’
mbrandizi
Great tutorial, thanks.
Just one addition: this can be used to open the LUKS volume in a non-interactive way:
echo "" | cryptsetup luksOpen /dev/sdb1 sdb1 -As you can see, the '-' tells cryptsetup to get the password from the standard input. This is useful for unattended scripts (eg, crontab). Of course, it isn't secure, if that password is on the same host where the volume is, but it might be reasonable if, for instance, it is (ssh) sent from a remote client that has to backup its local data. Indeed, I'm thinking of using this approach to auto-backup my laptop (where the password can be saved on a secure place like keepass, which is also accessible from scripts).
John
Thanks mate, this is very helpful and simple to follow
Blaise
Thanks for the tutorial! Could you elaborate on the purpose of the “test1.txt” and “test2.txt” files? It's not clear what difference using “sudo” has in this case, nor is it clear what this has to do with the drive being encrypted or not.
Average Linux User
You would not be able to create/place files without
sudobecause you had no permission for a regular user. After you change the ownership withchown, you can place files into encrypted folder withoutsudo