VeraCrypt: 4 ways to encrypt a flash drive in Linux
The information you store on your flash drives is the most vulnerable because you can lose it any day. So, you better protect the most sensitive data on your flash drive with encryption. In this post, you will learn how to encrypt a flash drive in Linux using four different ways with varying levels of complexity and security.
INTRODUCTION
Although nowadays everything is moving to the cloud and flash drives are not used often, they are still handy sometimes. Especially, if you are concerned about your privacy. Because your online accounts can get hacked, but in case of a flash drive, someone first needs to get physical access to it. And if your flash drive is encrypted, that person would also have to decrypt it, which is not easy.
It does not matter if your stored data is not too important, you never know what someone else might do with it. In addition, it is also very simple to encrypt a flash drive in Linux.
So, in this post, you will see several options to encrypt a flash drive in Linux.
- The first option is to create an encrypted file container. This way, you can store both encrypted and regular data.
- Another option is to split your flash drive into two parts, so you will have an encrypted partition for your important files and another partition for less important files.
- If all your data are very important, encrypt the whole flash drive. However, with this method, you will have to use the encryption passphrase every time you use your flash drive.
- Finally, there is a possibility of creating a hidden encrypted volume. It is the best option if you have very sensitive data that requires maximun protecting.
As you can see, you have several options, it all depends on you and the level of security you prefer.
VIDEO TUTORIAL
For all the encryption options, I will use VeraCrypt. It is the most user-friendly and flexible encryption tool. First of all, it is available for all platforms. So, you will be able to access your encrypted data from Linux, Windows, and Mac OS. Besides flash drives, VeraCrypt can be used to encrypt Linux hard drives too. The program has a fairly simple but powerful graphical interface.
1. Encrypt with a file container
Create an encrypted file container
To encrypt a flash drive in Linux with a file container, it is necessary to create a container. So, you need to click on the Create Volume button.
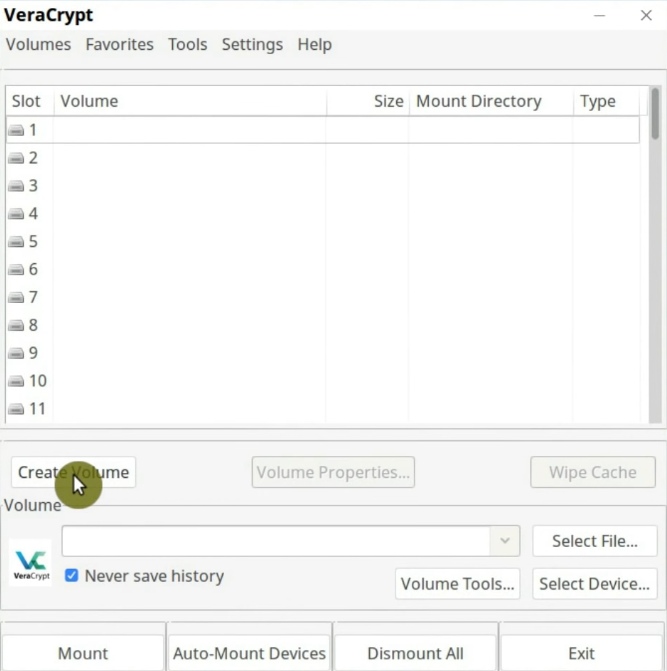
First, you have to select the Create an encrypted file container option in the following screen.
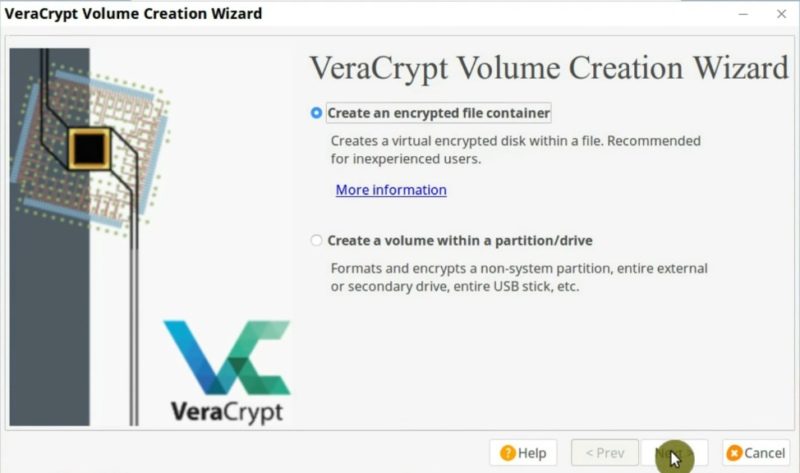
In this case, we will use the standard VeraCrypt volume option. I will show the Hidden Volume option later in this post.
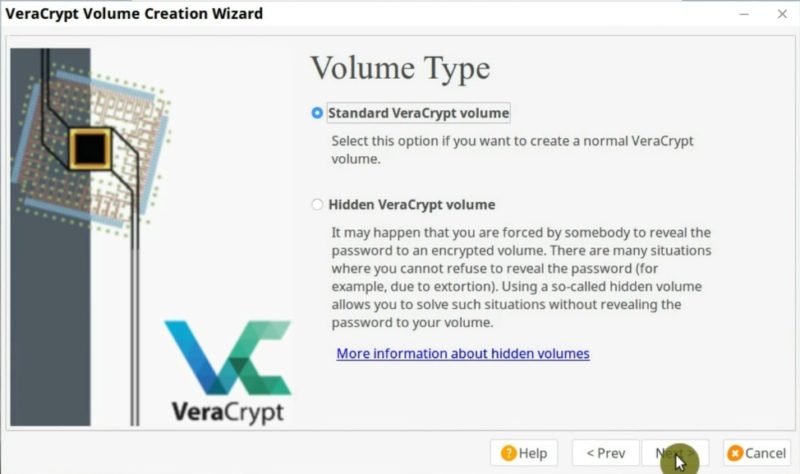
Now, you have to select the location and give a name to your encrypted volume. For example, I will name it “EncryptedVolume” and place it on the flash drive. Of course, you can choose the name you want. Then, click on the Next button.
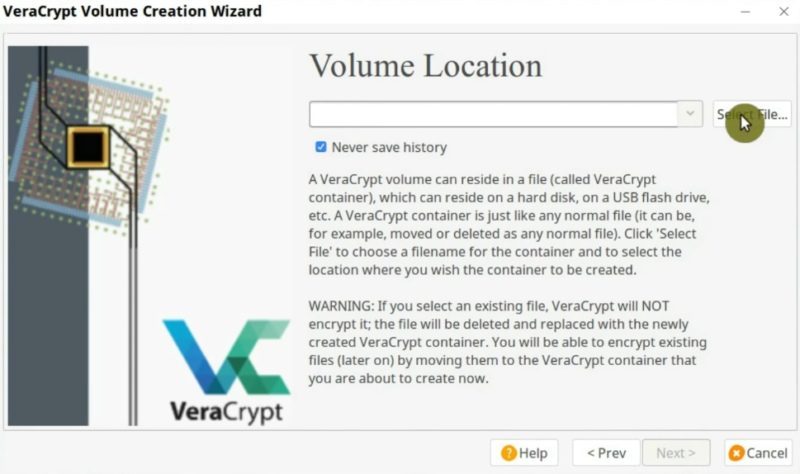
On the next screen, it is necessary to define the encryption algorithm. The default AES algorithm should be fine.
Now, you need to decide on the size of the encrypted volume. You will see the maxim available size, it is 14.7 Gb in my case. Choose the size based on the amount of data you intend to store in this encrypted volume. I will create one of 1 Gb size.
Next, you have to set a password for the volume. Try to make is reasonably long and include letters, numbers and special characters.
For the flash drive encryption, using a key file is not practical. But if you are going to mount your flash drive to 1-2 specific computers only, you can enable the key file to increase the security. I have shown how to use a key file in the post about Linux graphical encrypting program.
I recommend keeping the FAT file system for the encrypted volume as it will work across all operating systems in spite that you encrypt a flash drive in Linux.
On the next screen, you need to move your mouse randomly until the bar is filled in the next screen. This is done to generate random numbers for better encryption. When the bar is filled, click on the Format button.
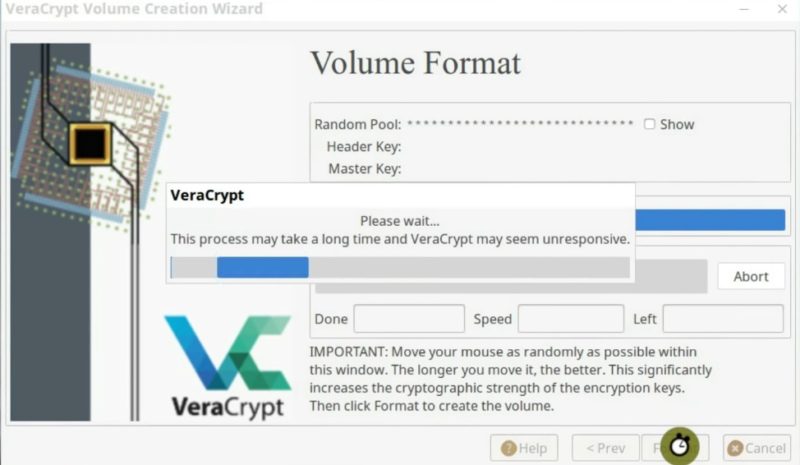
Now, VeraCrypt will create an encrypted volume on your flash drive. It may take a while, depending on the size of the volume you are creating. If all goes well, you should see this screen where it says that the volume has been created correctly.
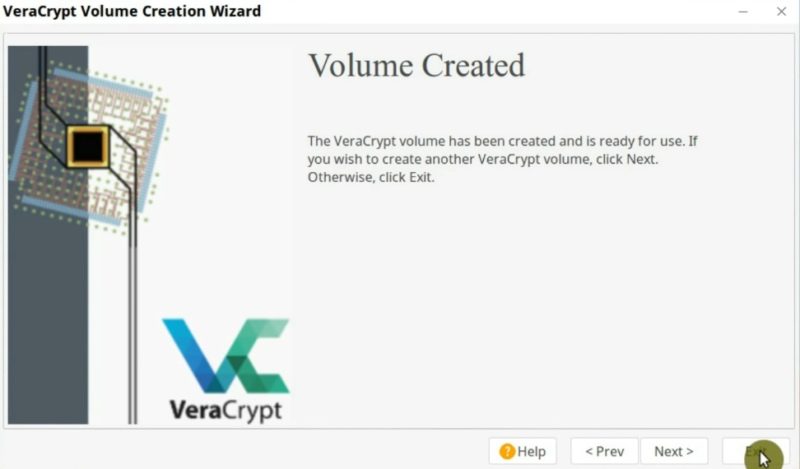
Mount the encrypted file container
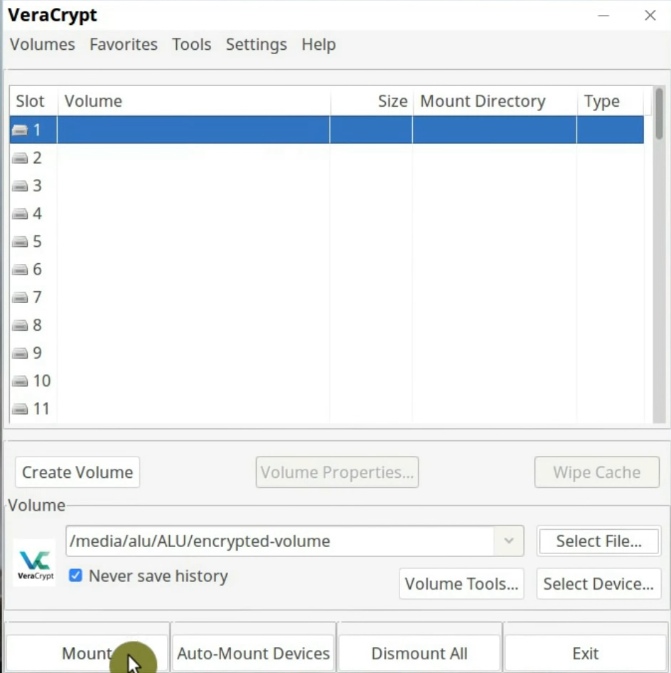
Now, I am going to test this encrypted volume. To mount the encrypted volume, go to the main window of the program and click on any free slot. Then select an encrypted file container we have just created and click on the Mount button.
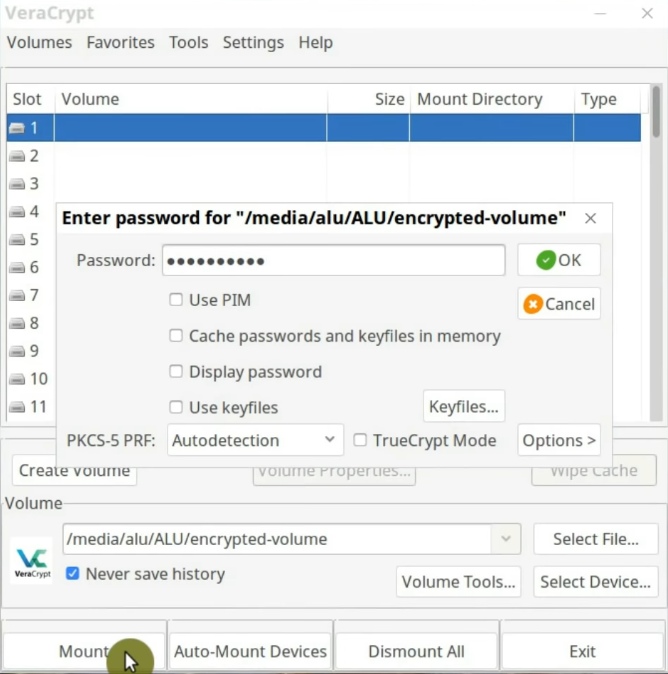
Now, you need to enter the encryption passphrase. You may also be requested to enter your administrative password.
Most likely, the encrypted file container will open in a new window automatically. If it does not, you should be able to find it in the Devices section of your file manager.
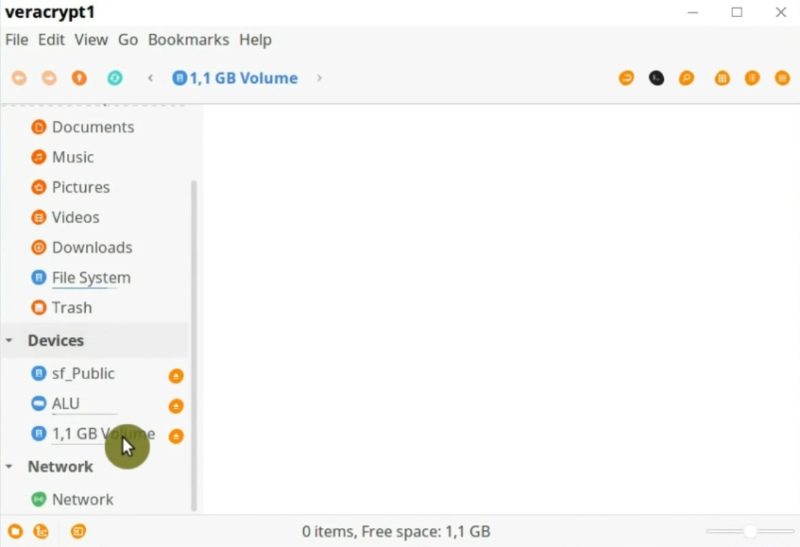
Test the encrypted file container
To test the encrypted volume, you place there any files. After you finished placing the data in this encrypted volume, close it and dismount.
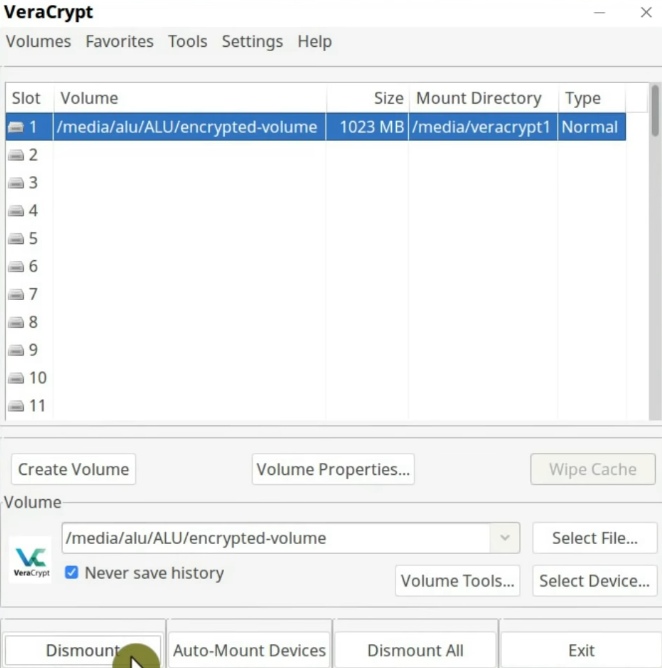
When the encrypted volume is dismounted, open the USB drive again. So, the file you placed into the volume should not be accessible in the flash drive. You should only see the encrypted volume file and even if you try to open it, the system should not recognize it. So, all the data located in this file is securely encrypted and the only way to access it is to mount it with VeraCrypt.
This was the easiest and the least paranoid way to encrypt a flash drive in Linux. The only problem here is that the encrypted file container will be visible to anyone who mounts your USB drive.
2. Encrypt with an encrypted partition
One way to hide the encrypted part is to split your flash drive into two parts, one will be encrypted and not visible by default, while another part will be a regular partition. To do that you need to re-partition your flash drive.
Re-partition your flash drive
You can use Disk Utility, Gparted or any other partition program. In this case, I will use Disk Utility. Open it from the main menu.
First, delete your partition.
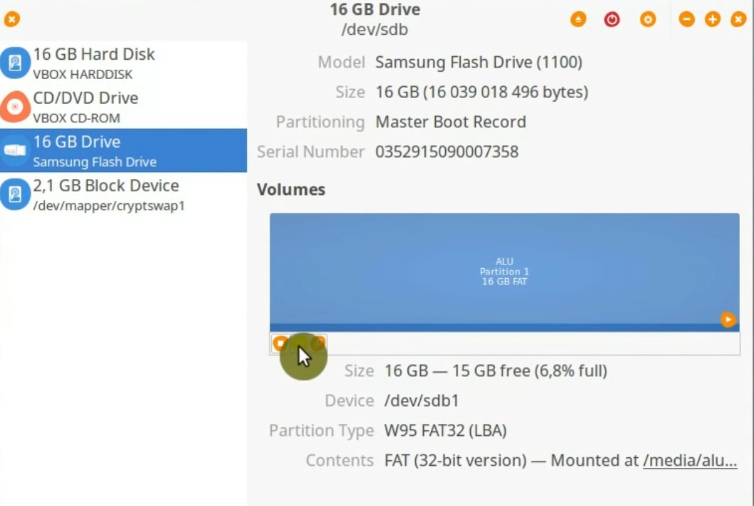
NOTE: This will also remove all the data from your USB drive. So make sure you copied it somewhere else before this step.
Next, you have to create one main partition that will be your regular partition. You probably would like it to format it with the FAT file system.
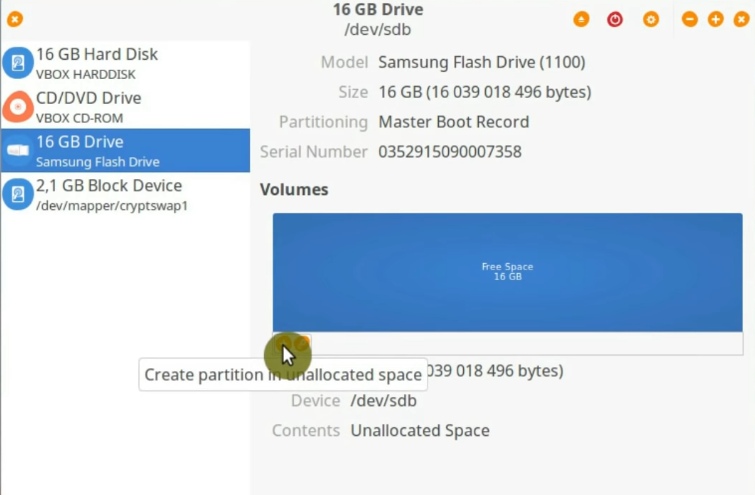
Now, you should see one partition and some free space which we will use for the encrypted partition.
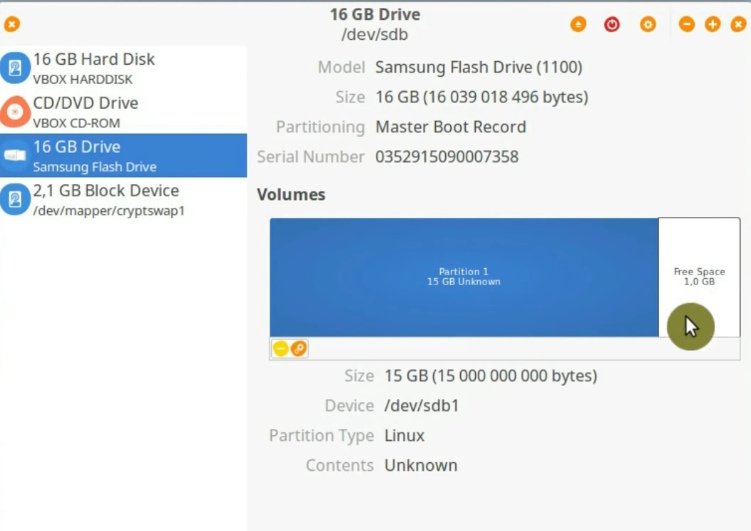
Click on the free space and create the second partition.
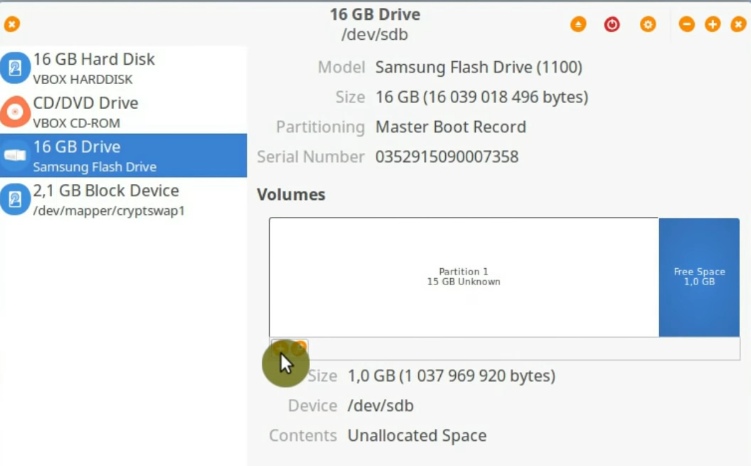
The file system does not matter here, it will be re-formatted anyway. Do not assign any name to it. This way it will look less obvious that there is some information in this partition. When this
Encrypt one partition
Go back to VeraCrypt and click on the Create Volume button. And instead of the File container option, select the Create a volume within a partition/drive option.
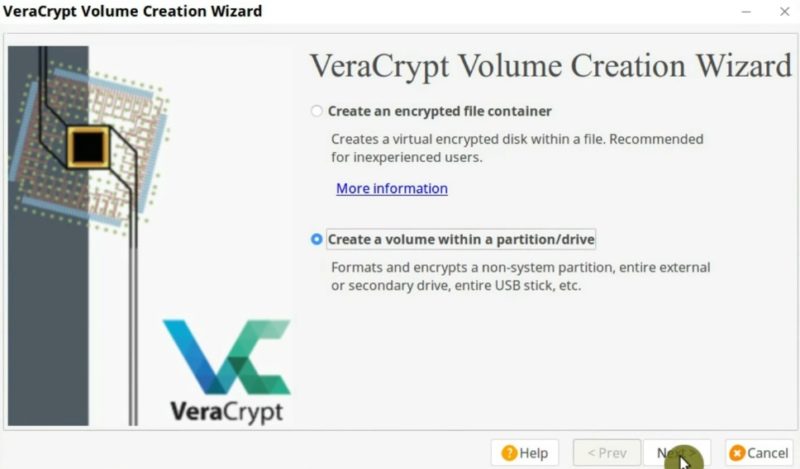
Keep it as a standard VeraCrypt volume and select the partition you want to encrypt.
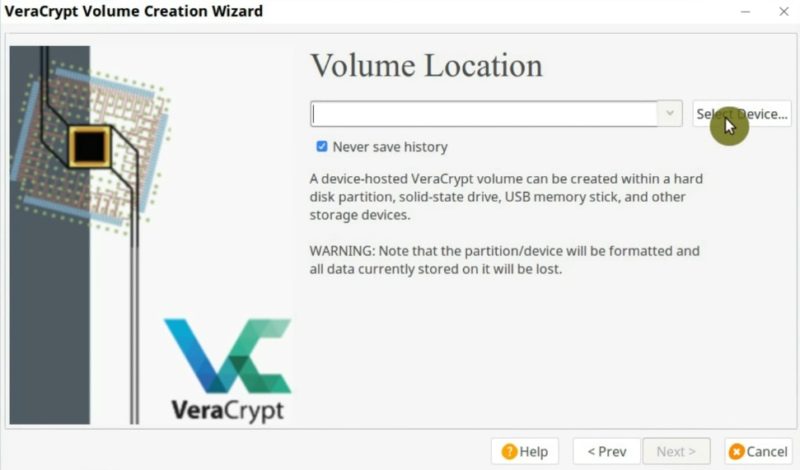
In this screen, you can see that sdb is my USB drive because of its size. And sdb1 and sdb2 are the two partitions we have just created. We need to encrypt the second one. In you case, the device name may be different. For example, it can be sdc2, sdd2, sde2, etc. Just looks at the size of available partitions and select the needed one.
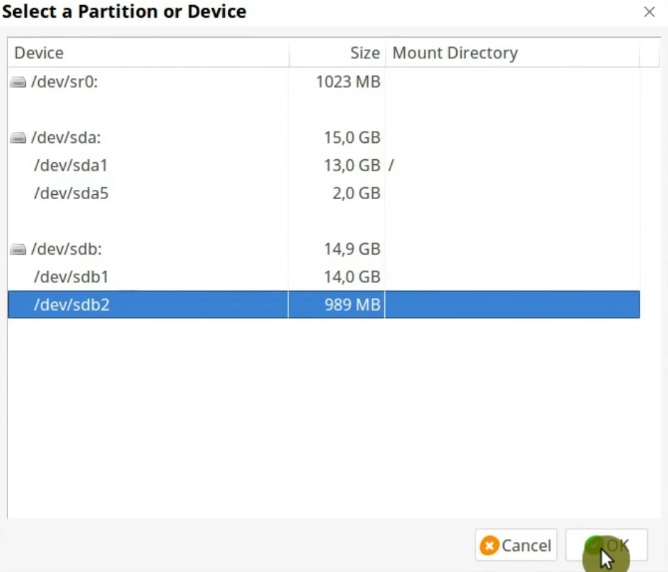
The next steps are the same as before. First, select the Encryption algorithm option, set the passphrase, select the FAT filesystem, and move the mouse to get randomness and format the volume.
When the volume has been created, check how the system sees it. In the file manager, if you look at the Devices section, you only see the first FAT partition and the encrypted partition is not shown. The Linux systems and I believe other systems will not show this partition in a file manager because the file system of this partition is not recognized.
There is only one way to see the encrypted partition: you have to mount it with VeraCrypt.
Mounting the encrypted partition
The mounting process for an encrypted partition is very similar to the mounting of an encrypted volume, you have seen above. There are a few differences.
After the device is mounted, you should be able to to find the encrypted partition in the Devices section of your file manager. You can select it and start placing files into this encrypted partition. When you finished, do not forget to unmount it.
So, this encryption option is one level more secure than a file container because someone who wants to get access to your data also needs to know about this partition and also needs to know that it is encrypted.
3. Encrypt the whole flash drive
Similarly to the previous method, you can also encrypt the whole flash drive in Linux. The difference from the previous option: you do not split your flash drive into two partitions.
This is the less practical way to encrypt a flash drive in Linux because the only way you can use your flash drive is to mount it with VeraCrypt. So, you will not be able to place any file on it any other way.
4. Encrypt with a Hidden encrypted volume
All these three options are to protect your data if you lose your flash drive. However, you may also need to hide the information that you have some encrypted information on the flash drive. You can use a hidden encypted volume.
Basically, you create one encrypted volume within another one. So, you can disclose the password from the outer partition that does not have any sensitive data. So, you can reveal the password, but you do not disclose the truly encrypted data, you only give access to your falsely encrypted data. The data you are really hiding is still encrypted.
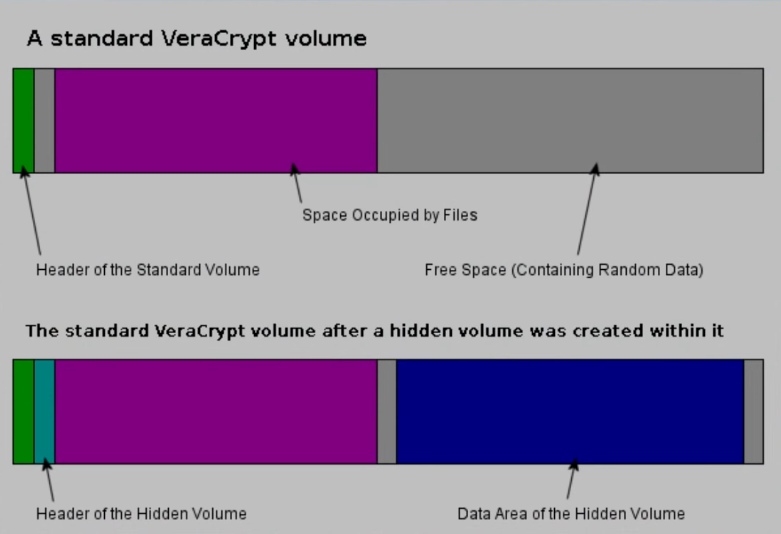
So, lets encrypt a flash drive in Linux with a hidden volume.
Create the falsely encrypted volume
First, create a new volume by clicking on the Create Volume button. After that, select the Create a volume within a partition/drive option and in the Volume type window select the Hidden VeraCrypt volume option.
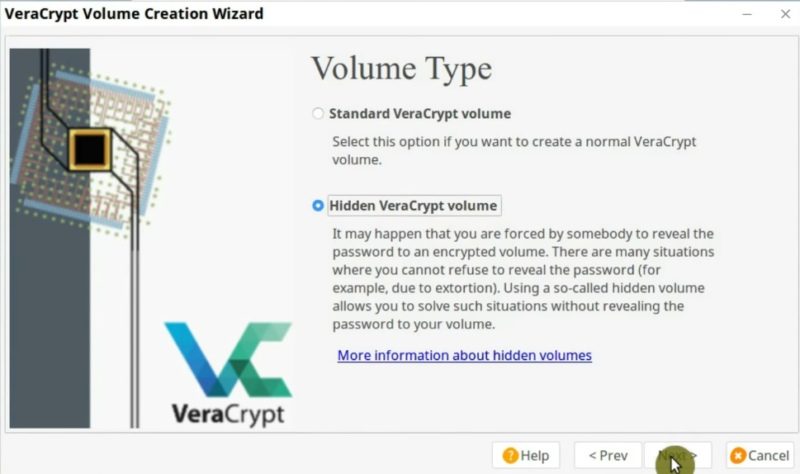
Similar to the encryption procedure described above, select the device you want to encrypt and choose the encryption algorithm.
Now comes the different part. In this case you have to create two passwords.
First, you create a password for the outer volume. This is so-called your falsely encrypted partition. You can use a simple password here because it is not important. This is a password you can reveal.
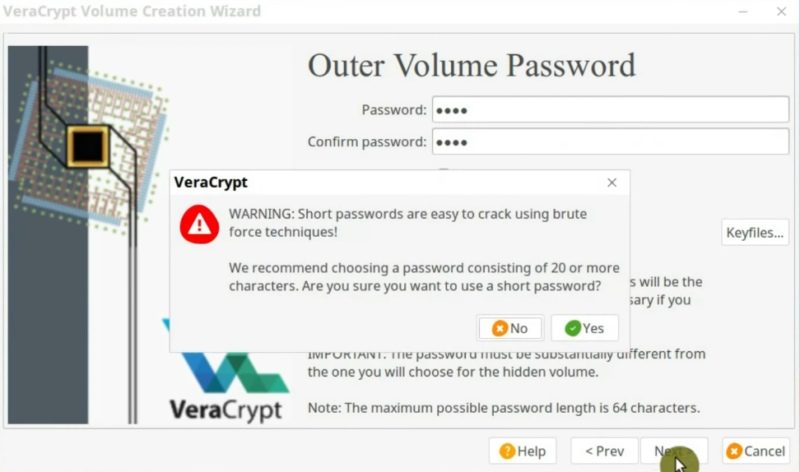
You can read more about the outer volume on the screenshot below.
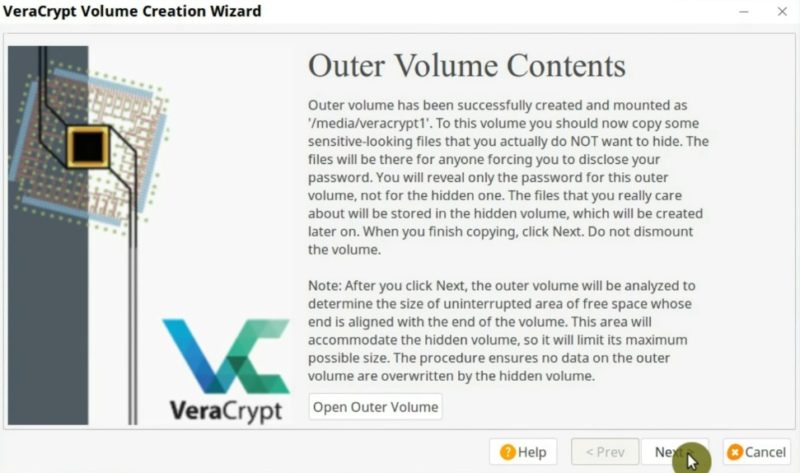
Create the hidden encrypted volume
In the next step will promt you to create a real encrypted volume where you store the data you want to hide.
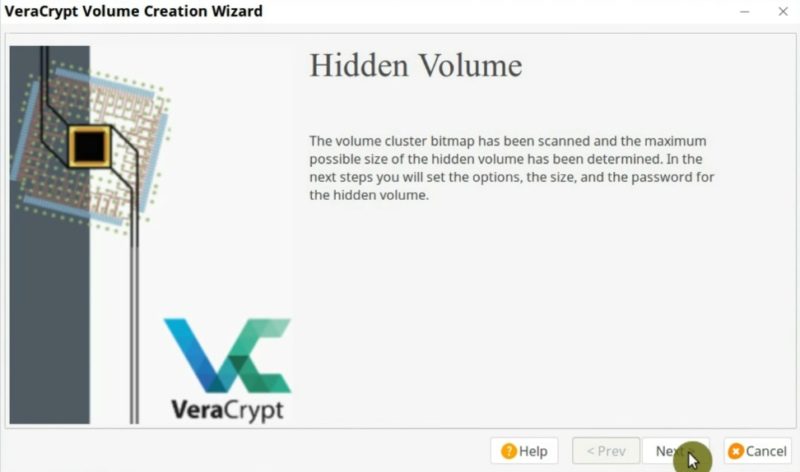
First, select the encryption algorithm for the hidden partition. Then, you specify the size of the hidden volume.
After that, you have to enter the real passphrase. It is better to make it long complex.
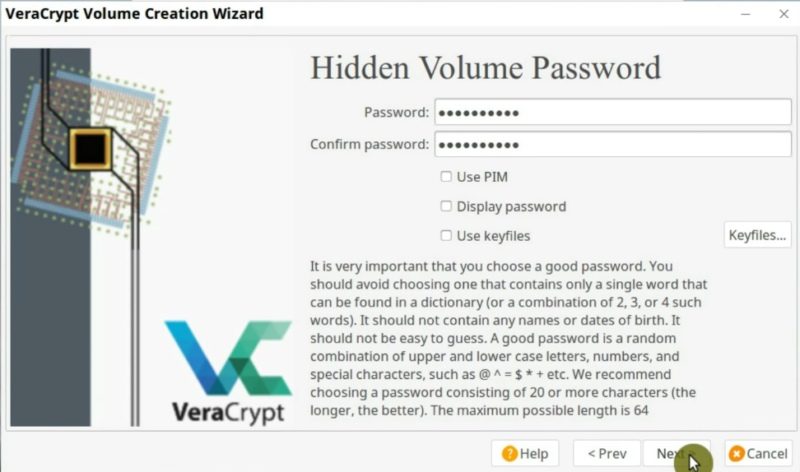
Next, on the Format options screen, select the filesystem type. Finally, format and create the volume.
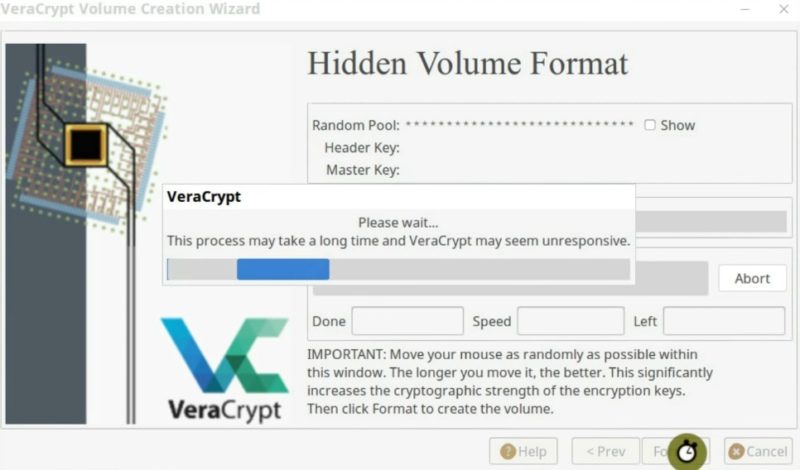
So, the hidden volume has been created. Let us test it.
Test the hidden volume
First, select a slot and mount the encrypted partition as it was shown above. You will be asked to enter the password. Now, depending on what password you enter, different volumes will be mounted. For example, I enter my longer passphrase. This password will mount the real hidden encrypted partition. On the other hand, if I use my shorted password, the fake encryption volume will be mounted.
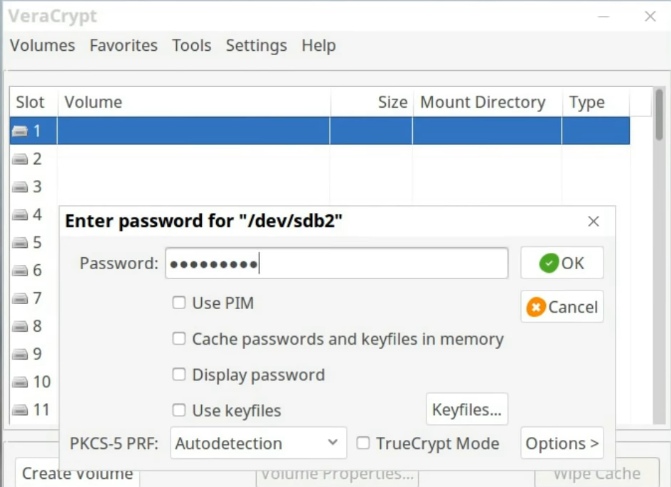
So, now everything depends only on what passphrase you use to mount an encrypted partition. Just be careful not to reveal a wrong passphrase if unluckily you happen to have to reveal your passphrase.
CONCLUSION
Now, you know four ways to encrypt a flash drive in Linux, for the cases if you lose it or even if you are forced to reveal a password from an encrypted volume. So, you can sleep well at night and do not worry about your data being insecure.
I also have a post about Make a bootable USB drive on any Linux distro.
 Never miss a post from us, subscribe to our newsletter
Never miss a post from us, subscribe to our newsletter
Comments
user 12345
how can i avoid saving decrypted data on my hard drive? I use Ubuntu, when i mount the USB stick its copy the data in computers drive or RAM, and i can still access the data without USB stick plugged in the PC.
Average Linux User
Do not move the data from the container. Some data can be extracted from RAM, to avoid that you need to encrypt your RAM too.
Gokhan Akkoyunlu
Hello there, I have just discovered your site. You can test the Cryptomator program. I use it. onedrive, gdrive, dropbox etc. I wish success to you.
Average Linux User
Thanks for another great tip. I will test Cryptomator. It looks very promising.