How to use SSH Key authentication in Linux
SSH keys provide a simple and yet extremely secure way to connect to a remote computer or a server. In this post, you will learn:
- Why use SSH keys
- How to create SSH keys
- What’s the difference between private and public keys
- How to add SSH keys to a remote computer
- How to disable password login and allow only the SSH key login
- How to use SSH keys for password-less login
- How to use SSH authentication agent
To securely test this SSH configuration, I recommend trying these settings in VirtualBox first.
Why use SSH keys
The short answer is SSH keys are more difficult to crack.
If you read my previous post where I explained how to install and use SSH, you know that SSH can be safely used with a password. But to be secure, you need to use a long and complex password. Nevertheless, many passwords still can be cracked with a brute-force attack.
On the other hand, SSH keys are much more complex than any password, and the need for two matching keys, a private and public, make it almost impossible to crack your SSH connection. So, by using SSH keys you will have the highest level of security on your server or a remote computer.
How to create SSH keys
To create SSH keys, run:
ssh-keygen
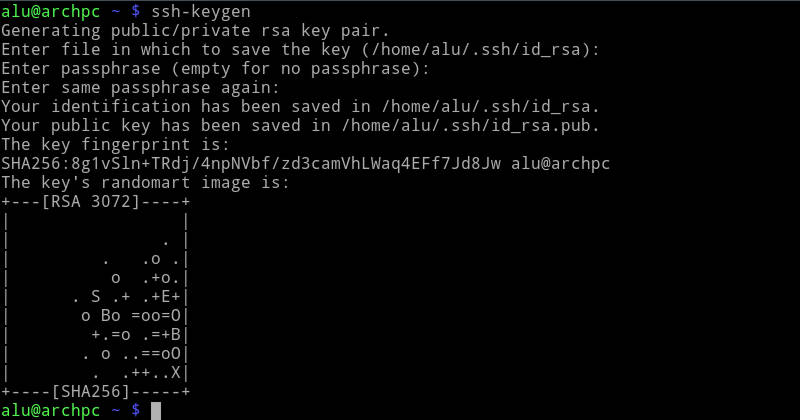
The program will ask you where to place the key and how to name it. By default, SSH keys are located in /home/username/.ssh/. You will also need to create a password for this key. For a passwordless log in, you can leave the password field empty and press enter.
If you get a warning that a key already exists, do not overwrite it because you will lose your current key and thus you won’t be able to authenticate to the SSH connection you use the current key for. You can simply rename the key.
You can find your newly created keys in ~/.ssh folder:
ls ~/.ssh

What’s the difference between private and public keys
I recommend using SSH keys not only because they are more complex than any password, but also because SSH key pair provides a cryptographic locking mechanism. You need both keys for authentication.
The public key, which name ends with .pub, is used for encryption. And it is stored on a remote computer. While the private key, is the key you keep on your local computer and you use it to decrypt the information encrypted with the public key.
I will not go into detail of cryptography because I am not an expert in cryptography. But in simple words, a public key encrypts the message of the remote server and the private key decrypts it and allow you to connect.
How to add SSH keys to a remote computer
To enable SSH key encryption, you need to place a generated public key to the remote computer. There are different ways to do that. I will show you all the possibilities and you chose the most suitable for you.
ssh-copy-id
The simplest one is to use ssh-copy-id:
ssh-copy-id -i ~/.ssh/id_rsa.pub username@serveraddress
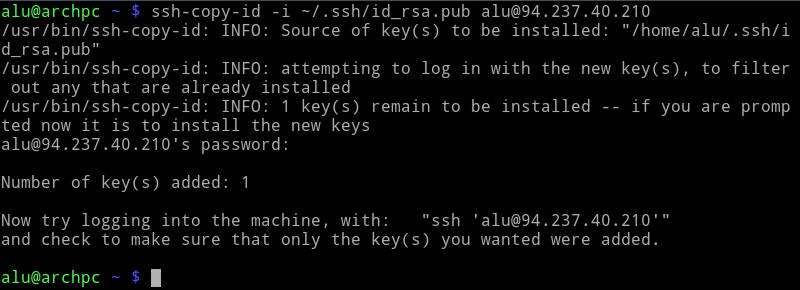
It will copy your public key to the authorized_keys file in ~/.ssh folder of the remote computer.
scp
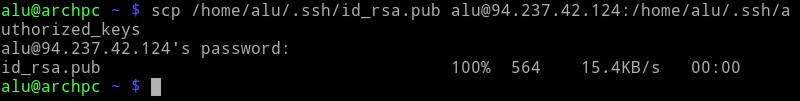
You can also use the scp command I showed in the previous post on SSH:
scp ~/.ssh/id_rsa.pub username@serveraddress:~/.ssh/authorized_keys
Append with cat
If you already use SSH keys on the remote computer, you should not use the scp command, because it will overwrite existing authorized keys. Instead, you need to append the public key to the authorized keys file with this pipe:
cat ~/.ssh/id_rsa.pub | ssh username@serveraddress "cat >> ~/.ssh/authorized_keys"
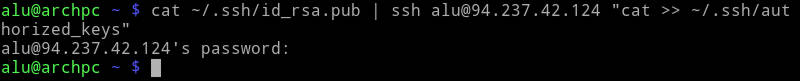
I showed how to use Linux pipes in this YouTube video.
Copy-paste
The best way to see what happens when you copy the public SSH key to the remote server is to copy and paste the public key by hand.
I recommend you to watch the video at the beginning of this post as it shows it much better than I can describe in words. However, if you keep reading, you simply need to copy the content of the public key in your local computer:
Log in to the remote server, open the file ~/.ssh/authorized_keys with any text editor, and paste the copied public key there:
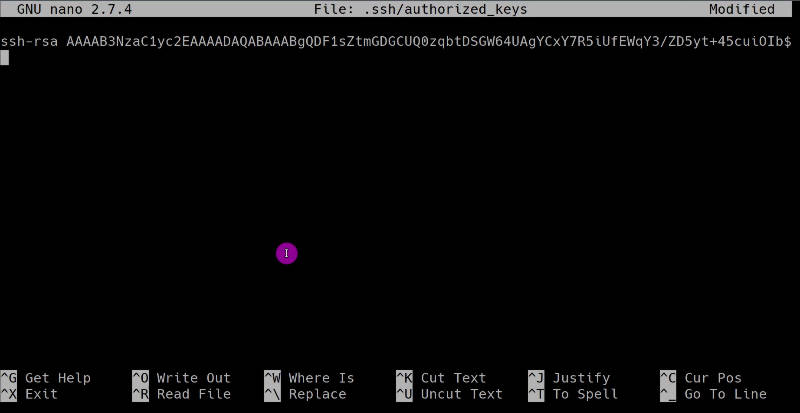
This is similar to what happens when you run ssh-copy-id, scp, cat from above.
So, you can manually copy-paste the public key, but it is not recommended because you may accidentally change the key content and your key pair won’t work.
GUI
Sometimes when you use virtual private servers, you can add SSH keys during server deployment with a graphical interface in your dashboard:
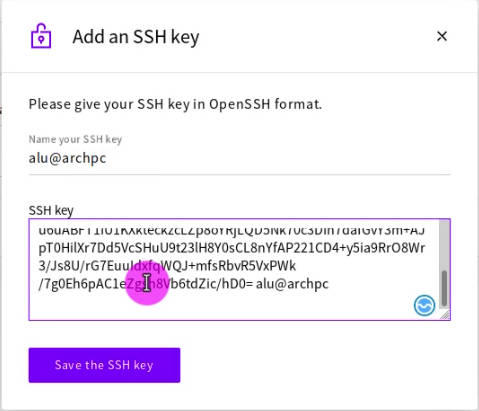
SSH key log in
So, after you added a public key, try to log in to the remote server. Instead of your regular password, you will need to type your key passphrase:
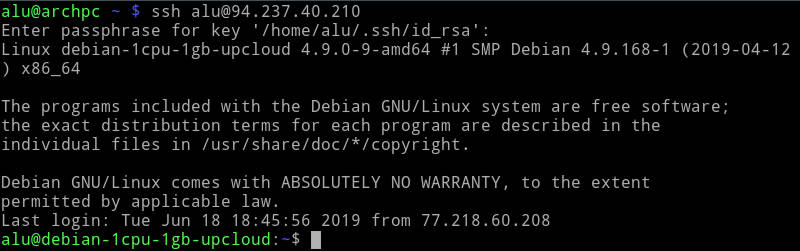
And you will be connected with an extremely high level of encryption.
How to disable password login and allow only the SSH key login
After you added an SSH key, it is advised to disable the password-based login and keep only the SSH key login. Otherwise, SSH keys become useless.
To that end, open the SSH config file on the remote server:
sudo nano /etc/ssh/sshd_config
Search for PasswordAuthentication and disable it:
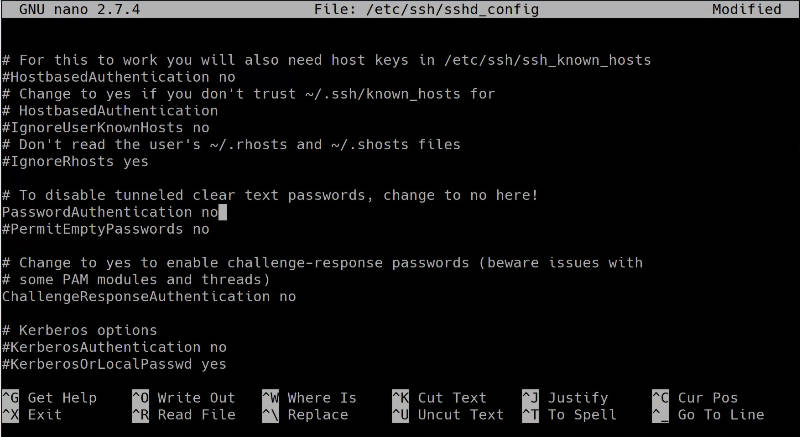
If you use Nano editor, you can use the shortcuts:
- Ctrl+W to search in file.
- Ctrl+O to save the changes
- Ctrl+X to exit the editor.
After you have done that, restart the ssh server:
sudo systemctl restart ssh
From now on, you have to use your SSH key passphrase only and you won’t be able to login with your user password. Also, when you try to login from an account that doesn’t have a matching private key for description, you will see the error Permission denied (publickey).
Now, your system is pretty secure. There are some additional security measures you can apply and I will show them in the next post. So, Subscribe for Blog Updates and you won’t miss them. But adding an SSH key and disabling password-based login is one of the most important security measures you could do.
Note, if you delete your private key somehow, you will lose access to the server. So, always backup your private keys to a secure place.
How to use SSH keys for password-less login
You can also use SSH keys for password-less login. To do that, you simply leave the passphrase empty when you generate the keys. So, you will only need a private key to log in. When you try to log in, you will log in without a request for a passphrase:
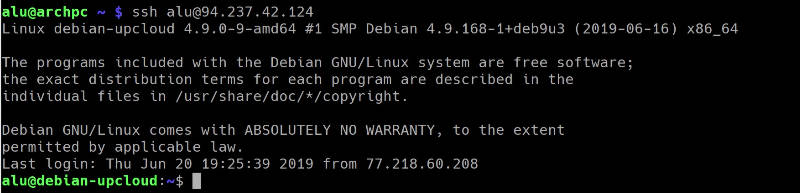
I know many users like this approach because it is a lazy way. But it is also less secure! if anyone gets your private key, they will get access to your server. Whereas if your key is password protected, they would also need to decrypt the key file. So, I show it as an option, but I do not recommend it. Instead, I would like to show you another sort of password-less login but a secure one. It uses the SSH authentication agent.
How to use SSH authentication agent
The SSH authentication agent allows you to enter your private key passphrase once and it will save it for the whole login session.
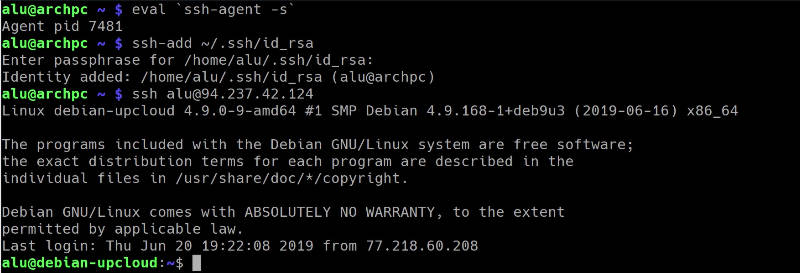
You need to start the SSH agent and add the key:
eval `ssh-agent -s`
ssh-add ~/.ssh/id_rsa
You will need to enter the passphrase of the key only once when you add the key to the agent. The SSH agent will keep the key decrypted in memory until you log out. So, if you try to log in to your server, you will log in without entering a passphrase and you can do that as many times as you need.
If you have several SSH keys and you need to use them with different servers, you need to create file ~/.ssh/config and pair your keys and servers with Host and IdentityFile:
# global options
User alu
# to make all ssh clients store keys in the agent
AddKeysToAgent yes
Host 94.237.42.124
IdentitiesOnly yes
IdentityFile ~/.ssh/id_rsa_vps
Host github.com
IdentitiesOnly yes
IdentityFile ~/.ssh/id_rsa_github
I find the SSH authentication agent particularly useful when I use SSH keys with Github. If I push commits several times per day, it gets really annoying to type the passphrase every time. Luckily, I do not have to do that thanks to the SSH agent.
Conclusion
I hope you will start using SSH keys if you have not yet. I also hope you have learned something new about using SSH keys even if you used SSH keys before. Thank you for reading.
 Never miss a post from us, subscribe to our newsletter
Never miss a post from us, subscribe to our newsletter
Comments
Chris
i have generate ssh key on A server for communicate server B. then i can able to do ssh with out passwd to server B.
but when i try to login in Server B . ..then trying to do ssh to server A ..it is asking password..why lit happens ?
it should be vise versa ..rt ? server A – server B , Server B- server A
Thanks
Jonathan Proaño (@parlox)
Thanks for this guide. It helped me understand some details I didn't figure out the first time I attempt to user keys for SSH. I know you said it doesnt' cover everything but I would say that it is very useful. Thanks again!
Average Linux User
Thank you for the feedback.
guest
Something else. Iptables probably not use DNS. So we need create script which will refreshed iptables rules with the new IP address from DNS. DNS or if you like better name “fully qualified domain name” (FQDN).
guest
Hi! Configuration ssh is a very big problem.
Average Linux User
Thanks for a useful list. I agree that this post doesn't cover everything. It is a simple intro to how to get SSH working. If one included everything you listed, it would become a full manual and not a blog-post :) I also cover some additional things in other post. For example, SSH keys post