Configure a One-time Password on Ubuntu
To enhance the security of your Ubuntu, you can configure a two-factor authentication with a one-time password on Ubuntu for login, ssh connection, and even the sudo command. One-time password (OTP) also known as 2-Factor authentication is probably the simplest security enhancement you can configure and yet it is one of the strongest protection of your system.
Content
- What is a One-Time Password (OTP)?
- Configure a One-Time Password on Ubuntu
- Disable one-time password on Ubuntu
- Recover from a One-Time Password lockout on Ubuntu
- How Secure is OTP on Ubuntu?
What is a One-Time Password (OTP)?
The One-Time Password (OTP) is a highly secure authentication method that uses a dynamic password in addition to your standard static password. During every login, a user enters a standard user password, and then there is a request to enter a one-time password. This one-time password changes every 30 seconds and it is generated with a help of a mobile app, thus it provides a two-factor authentication that is extremely difficult to break.
Configure a One-Time Password on Ubuntu
To configure a one-time password on Ubuntu, you need to do these steps.
1. Install Google Authenticator on your Ubuntu
There are a few packages that can be used to configure a one-time password on Ubuntu. I think Google Authenticator is one of the most popular and easy to use.
Run this command in your Ubuntu terminal, to install Google Authenticator:
sudo apt install libpam-google-authenticator
You can also use the Synaptic package manager if you prefer the graphical installation process over the command line. Search for libpam-google-authenticator in Synaptic and install it.
2. Install OTP mobile app on your phone
There are plenty of OTP apps, I have tried only Google Authenticator and andOTP.
You can use the Google Authenticator if you have iOS. Just be careful, because if your phone breaks or you lose it, you won’t be able to recover your Google Authenticator app and all the passwords stored in it.
For Android, I recommend installing andOTP because it is free and open-source. I also like it for its multiple backup options.
Install andOTP app on Android:
3. Activate Google Authenticator
To configure and activate Google Authenticator, run this command in the terminal of your Ubuntu:
google-authenticator
When you see a QR code on the terminal screen, scan it with your mobile OTP app:
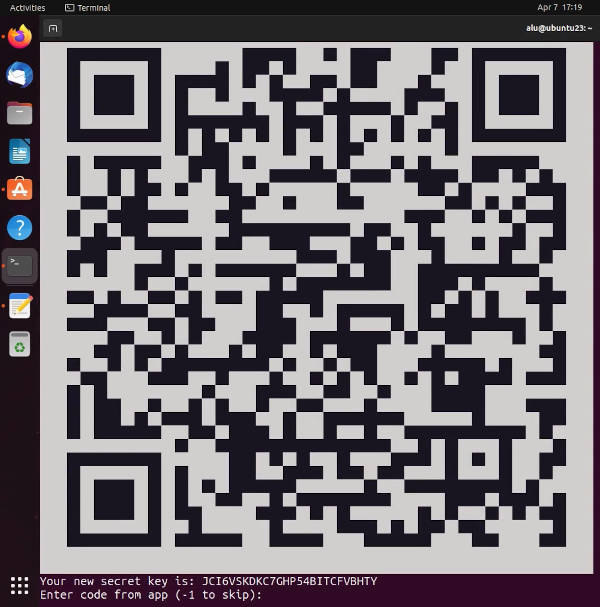
Type the one-time password from the OTP client and press enter to confirm the link of the OTP client with your Ubuntu.
You will also be presented with the emergency codes on the screen. Write them down in some secure place. You would need them in case you lose access to your mobile OTP app, so store them on some third device, i.e. not your Ubuntu or mobile phone.
Then you would need to answer a few questions to complete the configuration. I recommend answering yes to all of them.
4. Enable One-Time Password on Ubuntu
A one-time password requirement can be configured on Ubuntu to be system-wide so it is required for login and any administrative command with sudo. However, I find using a one-time password every time I need to use the sudo command a little bit inconvenient. I prefer to have a one-time password request only for login and remote access through SSH and Thinlinc but not for sudo.
Below I show how to configure a one-time password on Ubuntu for these scenarios.
Enable a One-Time Password System-Wide
To enable a one-time password on Ubuntu for login and any sudo command, open this file:
sudo nano /etc/pam.d/common-auth
And add these lines at the end of the file:
# to enable OTP
auth required pam_google_authenticator.so
You can also add the nullok option in the same line to allow a login for users who haven’t configured a one-time password for their account. It is useful if you administer a computer with multiple accounts.
Save and close the file by pressing Ctrl+O and Ctrl+X correspondingly.
Now, log out and try to log in. You will be prompted to enter a one-time password after you enter your user password:
The same happens when you use any sudo command in the terminal:
A one-time password would also be requested for any graphical admin action such as system update through the Ubuntu update manager:
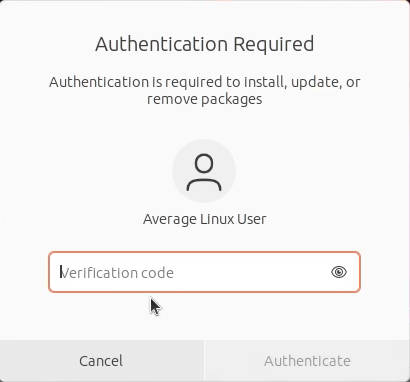
Disable One-Time Password for SUDO
To keep the one-time password requirement for login only and skip it for any admin actions, you need to add a one-time password request only to your login manager:
sudo nano /etc/pam.d/gdm-password
Add this line at the end of the file:
# to enable OTP
auth required pam_google_authenticator.so
If you have enabled one-time password system-wide in /etc/pam.d/common-auth (as described above), revert the changes by removing the line auth required pam_google_authenticator.so from it.
Enable a One-Time Password for SSH
Using a one-time password is especially useful for the SSH connection when your Ubuntu is open to the whole Internet.
Open the file /etc/ssh/sshd_config on your remote Ubuntu:
sudo nano /etc/ssh/sshd_config
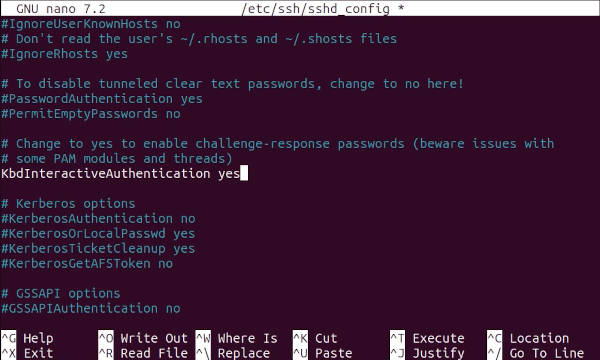
Find KbdInteractiveAuthentication and set it to yes.
Press the keys Ctrl+O to write the changes, and Ctrl+X to exit nano.
Next, open the common session PAM config file.
sudo nano /etc/pam.d/common-session
And add the OTP authentication requirement at the end of the file:
# to enable OTP
auth required pam_google_authenticator.so
To apply these settings, restart the SSH daemon:
sudo systemctl restart ssh
Try to log in with SSH, and you will be welcomed with this OTP request:
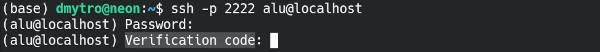
One-Time Password and Public key authentication for SSH
You may want to secure your SSH connection with One-Time Password authentication in addition to Public key authentication, to harden your SSH security even more.
In that case, you need to open /etc/ssh/sshd_config file:
sudo nano /etc/ssh/sshd_config
And modifying these three options to the following look:
PasswordAuthentication no
PubkeyAuthentication yes
AuthenticationMethods publickey,keyboard-interactive
Use the keys Ctrl+O and Ctrl+X to write the changes and exit nano.
Restart the SSH daemon to apply the settings:
sudo systemctl restart ssh
After these settings, you will be requested to provide a one-time password after you pass the public key verification step during the SSH login.
Disable one-time password on Ubuntu
If you have access to your OTP app and can log in to your Ubuntu system, to disable a one-time password on Ubuntu, you just need to revert all steps you have done. That’s to remove the auth required pam_google_authenticator.so line from /etc/pam.d/common-auth and /etc/pam.d/gdm-password if you edited them as described above.
Also, remove the .google_authenticator file:
sudo rm ~/.google_authenticator
Now, your one-time password on Ubuntu is disabled.
Recover from a One-Time Password lockout on Ubuntu
If you happened to lose access to your OTP app and the emergency codes, and you got locked out from your Ubuntu, you still can recover access to your system.
First, you need to reboot and access the GRUB menu. If you do not see it by default, hold the right Shift key during the boot process and you should get the GRUB menu on your screen:
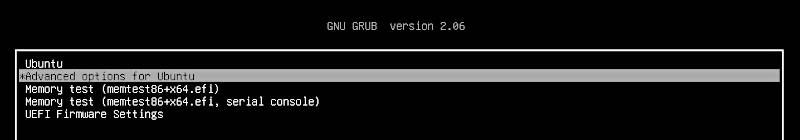
Go to the Advanced options for Ubuntu and then select the recover mode:
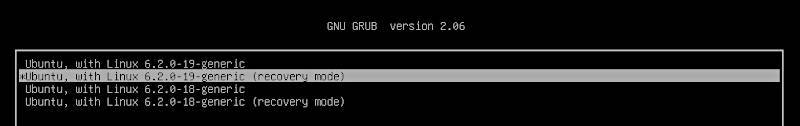
In the Recovery Menu, select root and press enter:
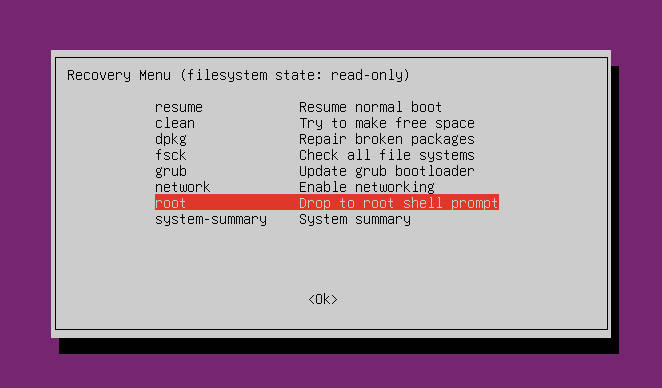
You will be asked to press Enter again for maintenance. Do that and you will get to the root account of your system. Now, you can remove the .google_authenticator file:
rm /home/username/.google_authenticator
Open /etc/pam.d/common-auth with nano:
nano /etc/pam.d/common-auth
And remove the auth required pam_google_authenticator.so line from this file. Remember to use the keys Ctrl+O and Ctrl+X to write the changes and exit the editor.
Do the same with the /etc/pam.d/gdm-password file.
After that, your login should get recovered from a one-time password lockout.
How Secure is OTP on Ubuntu?
As you can see from the description of recovering from a one-time Password lockout on Ubuntu, one can bypass OTP on Ubuntu if one has physical access to it. There are ways to make this bypass harder, for example, by protecting GRUB with password and encrypting the hard drive. However, these measures also do not give 100% protection. One can boot from a live USB to bypass the GRUB a password. Despite the encryption of a hard drive, the configuration file must be kept outside the encrypted section to permit access to the login process before decryption.
Thus, I see the OTP security enchantment useful only for the SSH connection.
 Never miss a post from us, subscribe to our newsletter
Never miss a post from us, subscribe to our newsletter